Mr Recorder Douglas Campbell QC:
Introduction
- The Claimant ("IPCom") is the proprietor of a portfolio of telecommunications patents which it acquired from Robert Bosch in 2007. This action concerns EP(UK) 2, 579, 666 B1 ('666, or "the Patent") which is entitled "Allocation of access rights for a telecommunications channel to subscriber stations of the telecommunications network".
- The Defendants are part of the same group of companies. Originally there was a plea of joint tortfeasance, but the parties have now agreed that this issue will be determined at a later date. I will refer to the Defendants simply as "Vodafone" without distinguishing between them.
- The Patent is part of the same patent family as EP(UK) 1, 841, 268 ('268, or as IPCom calls it, "100A") which has been extensively litigated in the United Kingdom, and which has been found to be both valid and essential to the 3G (UMTS) mobile phone standard. For instance I was referred to 3 cases where '268 was considered: Nokia v IPCom [2011] EWHC 1470 (Pat), Floyd J; the unsuccessful appeal from that decision, Nokia v IPCom [2012] EWCA Civ 567; and IPCom v HTC [2015] EWHC 1034 (Pat), Birss J. These were all cases about 3G mobile handsets. The present action is about Vodafone's network infrastructure equipment for 4G.
- The claim form was issued on 26 October 2018 and served on 22 February 2019, alleging infringement of '666 by Vodafone's 4G systems and also infringement of another patent, EP 2 378 735 ('735), by Vodafone's 3G systems. On 20 March 2019 IPCom issued an application seeking expedition. The upshot of that application was that on 13 May 2019, Birss J ordered that the issue of infringement in relation to '666 should be heard as an expedited trial ("trial A"). That is the trial before me. The issue of infringement in relation to '735 will be heard later ("trial B"), then there will be a further trial on FRAND issues after that.
- A key part of the reason for expediting the present trial was that the '666 patent will expire on 15 February 2020, and IPCom wanted a trial before then in order to obtain an injunction. However on 8 November 2019 Vodafone served an amended Product and Process Description ("PPD") and also further evidence relating to their allegedly infringing network infrastructure. This was referred to in argument as the "fundamental redesign" and its details are said to be confidential. The significance is that, as IPCom accepts, acts done in relation to the fundamentally redesigned system do not infringe '666 when it is operating in 4G. IPCom nevertheless considers that acts done in relation to this system can potentially infringe '666 for other reasons, as well as infringing other patents.
- It was against that background that on 13 November 2019 IPCom applied for its own expedited trial to be adjourned until after expiry of the patent, and for permission to amend its case so as to introduce new allegations of infringement, new patents, and a new claim to a post-expiry injunction. I refused that application on 18 November 2019, the first day of the trial window: see [2019] EWHC 3323 (Pat).
- The Patent is also the subject of a pending EPO opposition. For instance the EPO opposition division gave its preliminary opinion on 17 January 2019, and an oral hearing took place in September 2019. In order to meet certain points made in the EPO preliminary opinion, IPCom filed an application on 20 May 2019 pursuant to s 75 of the Patents Act 1977 for unconditional amendment to the claims as granted. It did so in order for this Court to consider such claims, even though the EPO proceedings would not be completed before this trial. At the oral hearing in the EPO, IPCom then had to offer still further amendments to the Patent in order for it to be maintained by the EPO in amended form. IPCom subsequently filed a further application to amend pursuant to s75 on 10 October 2019 for the same reasons as before (ie so that this Court should consider such claims), but only in the event that its first application to amend failed. The first set of amended claims was referred to at trial as the "unconditionally amended claims", and the second set was referred to as the "conditionally amended claims".
- IPCom has made it clear that it does not accept that any of these amendments are actually necessary, and that it intends to appeal the EPO Opposition Division decision once it receives the written reasons. IPCom also points out that whilst Vodafone has opposed both sets of amendments, Vodafone has not challenged the validity of each and every claim. For instance IPCom asserted the independent validity of unconditionally amended claims 5, 9 and 11 on 17 May 2019 and Vodafone served no evidence challenging them. This is probably because they were not alleged by IPCom to be infringed.
- The upshot of the above is that the issues I have to decide are as follows:
a) Construction of the unconditionally amended claims.
b) Allowability of the unconditionally amended claims.
c) Construction of the conditionally amended claims.
d) Allowability of the conditionally amended claims.
e) Obviousness in the light of the prior art.
f) Essentiality of both sets of claims.
g) Vodafone's non-infringement arguments in relation to its real systems. This includes two less commonly run defences: one of Crown use pursuant to s 55 of the Patents Act 1977, and one that any infringement was de minimis.
h) Vodafone's counterclaim for declarations of non-infringement.
- It will be seen that there were no material disputes as to either the identity of the skilled addressee or as to common general knowledge. This is probably because these matters were previously considered in the '268 cases and neither side sought to challenge the findings made therein.
- The case has no shortage of abbreviations, some of which have commonly used synonyms. For instance 4G is the common name for LTE, 3G refers to UMTS, 2G refers to GSM, and 2.5G is used to refer to GSM/GPRS.
The witnesses
- I heard oral evidence from one witness on each side, namely their respective experts. Dr Irvine appeared for IPCom and Mr Bishop appeared for Vodafone. Somewhat refreshingly, neither side directed any personal criticism at the witness for the opposite side. On the contrary, both sides accepted that both experts were personally doing their best to assist the Court. I agree. That said, Vodafone made several specific criticisms of the way in which Dr Irvine's evidence was given and IPCom criticised the way in which Mr Bishop had been instructed. I will therefore consider these criticisms.
- Dr Irvine is a Reader in the Institute of Signal Processing at the Department of Electronic and Electrical Engineering at the University of Strathclyde. He has been a full time academic since 1994, but he has also worked on the design, configuration, and deployment of a private research 4G network on Orkney. Vodafone submitted as follows.
- First, that Dr Irvine's own experience at the priority date was in resource management generally, and not in the grant of the particular access rights of the type with which the patent is concerned. I agree, but as Jacob LJ pointed out in Technip France SA's Patent [2004] RPC 46 the purpose of expert witnesses is to explain things, and for this purpose it does not matter whether they do or do not approximate to the skilled man. I found that Dr Irvine was good at explaining things.
- Secondly, that Dr Irvine had "masses" of patent litigation experience generally, into double figures, and that he found it difficult to exclude his prior knowledge of the '268 patent in particular. I do not consider that anything turns on this. Vodafone did not show me any examples of any Court ever criticising Dr Irvine's evidence. Nor did Vodafone even tell me whether Dr Irvine was on the winning or losing side in any of these cases.
- So far as his knowledge of the '268 patent was concerned, I can see why prior knowledge of a closely related patent might introduce an element of hindsight into the analysis of whether the '666 patent is obvious. However introducing hindsight would be more of a problem for a Defendant's witness (ie one relied upon in support of an attack on validity) than for a Claimant's witness. In any event I do not consider that Dr Irvine's evidence was tainted by hindsight.
- Thirdly, Vodafone submitted that in his cross-examination, Dr Irvine appeared to be approaching his evidence on the basis that the uninventive skilled person would have a 2:2 degree. Vodafone submitted that this level was plainly too low and that Dr Irvine had thereby assessed inventive step by the wrong standard. Whilst this is not quite what Dr Irvine said, I agree that there is force in this criticism and I will therefore treat Dr Irvine's evidence on this topic with some caution.
- Mr Bishop is now, and has been since 2013, an independent consultant with his own consulting company. He worked at Samsung Electronic Research Institute for 16 years starting in 1996. He became Director of Standards and Industry Affairs in 2011. His work at Samsung focussed on, inter alia, the development of the GSM, GPRS, UMTS, and LTE standards and he was particularly involved in the development of the 3GPP standard over the period 1998 to 2004. IPCom submitted as follows.
- First, that despite being expressly instructed to consider a prior art citation known as Farsta, Mr Bishop's conclusions on this topic had been edited out of his report. This does not take IPCom very far, since Vodafone did not rely on Farsta at trial.
- Secondly, that despite being put forward as a witness with relevant experience at the relevant time, including his knowledge of standards meetings in the years leading up to 1999, he had been instructed by Vodafone's lawyers not to refresh his memory as to what the skilled person would actually have known immediately before the priority date. Hence Mr Bishop's evidence about the state of the art in 1999 was based on his unassisted recollection of 20 years previously. Even though Vodafone's case did not depend on details of what was discussed in standards meetings I still found these instructions to Mr Bishop puzzling since his involvement in these meetings seemed to be one of the reasons why he had been chosen as Vodafone's expert in the first place. IPCom suggested one possible reason for this was that in the '268 case, Nokia's expert (a Professor Purat) had reviewed the relevant documents and found nothing in them to support Nokia's attack on validity of that patent. I do not find it necessary to consider whether this theory is correct.
- Mr Bishop also has general experience of working with standards, but that experience did not seem relevant to determining what the wording of the standards in this case actually meant.
- Thirdly, IPCom submitted that although Mr Bishop claimed to have formed his views on obviousness before reading the Patent, his report only contained a single homogenous section on obviousness which did not make it clear what his original views actually were. I agree that unless an expert produces a document containing his views in advance of seeing the Patent, and then exhibits that document, it will be difficult for the opposing party and the Court to know what the original views actually were. However even where this is done, such a document will only ever show what one real person's views were (and probably in an unfocussed manner at that) whereas the Court is trying to assess obviousness from the point of a view of a legal construct. In my view it is more important to focus on the substance of the obviousness case itself, rather than the method by which it was developed.
- Vodafone also relied on evidence from a number of fact witnesses, who were not required by IPCom to attend for cross-examination and whose evidence was therefore undisputed. These were as follows.
- Mr Lee Bradbury, a Senior Radio Access Network Operations Manager employed by Vodafone. He is responsible for the operation and maintenance of the Vodafone radio network, including 4G. His evidence went mainly to the Crown use defence.
- Mr Philip White, Vodafone's Coverage Solutions Manager. His role was to confirm the information set out in Vodafone's PPD, which by the time of trial was on its fourth version.
- There were 3 further witnesses representing the suppliers of base stations for Vodafone's network, namely Ante Mihovilovic (Ericsson), Antti Kuurne (Nokia), and Zheng Zhilong (Huawei). Their evidence went to the details of the fundamental redesign, and as such played very little part in the trial.
Skilled addressee
- It was common ground that the Patent was, like the '268 patent, addressed to an engineer or team of engineers concerned with developing mobile phones for use in the UMTS mobile telecommunications standard, and in particular in developing systems for control of access to the random access channel (RACH): see Floyd J, as he then was) in his judgment in the '268 case (ie Nokia v IPCom [2011] EWHC 1470 (Pat)) at [6]-[7]. This in fact refers back to an earlier judgment of Floyd J on another IPCom patent in the same family, known as the "parent 100 patent": Nokia v IPCom [2009] EWHC 3482 (Pat).
- Floyd J also held that those working on the 3G/UMTS project were "engineers of the highest calibre" and would know where to find relevant information in the relevant standards such as GSM, GSM/GPRS, IS-95, and the current state of UMTS. Vodafone accordingly submitted, without objection from IPCom, that the skilled addressee of the '666 patent is very skilled indeed. I accept this.
- More specifically, the parties agreed that the skilled addressee would have an undergraduate degree in electronic engineering or a related discipline. There were originally 2 minor additional disputes, about whether the skilled person would follow the technical submissions to the UMTS process and how much postgraduate experience in industry he (or, for all purposes, she) would have in industry. Nothing ever turned on either dispute and both were resolved by time of closing speeches in any event. The skilled person would be following these technical submissions closely, and would have at least 2 years of postgraduate experience.
Common general knowledge
- There was little dispute as to the substance of the relevant common general knowledge.
Previous findings by the Court
- The starting point is the useful summary originally produced by Floyd J in his judgment on the parent 100 patent, which was repeated in his judgment on the '268 patent at [8]. Both sides accepted that this was common general knowledge.
"8. Mobile telecommunications networks are complex structures. The general nature of such networks has been described in a number of judgments, and I do not need to repeat that exercise here. This case is concerned with how one controls access by the mobiles to a random access radio channel or RACH between the mobile and the base station (the "uplink"). In the parent case I said this about the technical background to the 189 patent. It is useful to set it out here as well:
Contention on a shared channel
Where the uplink from a mobile station is a shared random access channel, there is a danger of collision between users' signals, allowing stronger signals through and preventing weaker ones. This competition is called "contention". It can be tackled in numerous ways. One set of ways in which the problem is tackled is by restricting access to the channel.
The "lottery"
One well known way of restricting access to the channel involved a form of lottery. "Lottery" is not a term of art, but is a convenient term to provide an analogy for what is done. Each mobile station generates for itself a random number and compares it with a value sent by the network. A "win" can be defined as generating a random number greater than or equal to the transmitted value. So, for example, the possible transmitted numbers could be 1 to 10, and the random numbers could be 1 to 9. If the base station transmits a 10, no mobile will get onto the channel, but if it transmits a lower number than 10 an increasing proportion of mobiles can get on. At busy times the access can be throttled back to prevent collision. At very low usage times the transmitted value could be 1, and all mobiles would get access…
Access classes
Systems in which certain classes of user (user classes or access classes) could be restricted from access were also well known. For example class barring, under which a mobile of a particular class would be barred from access absolutely, was a feature of the GSM/GPRS system.
Transmission capacity
Bandwidth is a scarce resource in any mobile telephone system. Designers of such systems would try to arrange matters so as to minimise the amount of data that had to be sent routinely. One common general knowledge way of limiting the amount of data to be sent is the use of single bit flags, which alert the mobile to the fact that data is coming. This allows the network only to send the data when the flag is set."
GSM/GPRS
- I should say a little more about class barring in GSM/GPRS, referred to above. My attention was drawn to 3 different GSM specifications, namely GSM 02.11, GSM 04.08, and GSM 04.60. Dr Irvine explained access class barring within GSM as follows, in a passage of his evidence which was not challenged:
"28. Section 3.3.1.1.1 of GSM 04.08 specifies the method for determining whether the mobile in question is granted permission to access the network. It explains that each user is allocated to an access class. The allocated access class is stored on the SIM. There are 10 normal access classes, access classes 0 to 9. These are randomly allocated based on the last digit of the International Mobile Subscriber Identifier number (the "IMSI"), which is essentially a SIM Card identifier. There are approximately equal numbers of users in each of access classes 0 to 9. In addition, some special users are also allocated to additional special access classes 11 to 15. GSM 02.11 (now TS 100 921) defines the special access classes as being for the following high priority users:
Access Class 15 for PLMN Staff. "PLMN" stands for the Public Land Mobile Network and is just the network operator;
Access Class 14 for the Emergency Services;
Access Class 13 for Public Utilities (e.g. water/gas suppliers);
Access Class 12 for the Security Services; and
Access Class 11 for PLMN use (for example, for test mobiles while setting up a cell).
29 Section 3.3.1.1.1 of GSM 04.08 states that the system can instruct mobiles in particular access classes not to make access attempts by sending a list of "authorized" access classes. This allows the load on the access channel to be varied between 100% and 0% in steps of roughly 10%. When the load on the access channel is controlled, some user classes will be able to access the system, whereas other user classes will be denied any access to the system. The system is referred to as class barring."
- It will be seen that in GSM, class barring was a relatively crude concept – either everyone in a given class was barred, or nobody. If the class to which the mobile belonged was not barred, then the next step was to request network access.
- Each access class was represented by a single bit (ie there were 15 in total, as well as an additional bit for access class 10 which is not relevant for these purposes). Even if the access class to which the mobile belonged was allowed access, it did not follow that the individual mobile itself would be granted access. Dr Irvine explained that the mobile would allow a random number of time slots to pass before first requesting access. If the network did not have sufficient resources to grant access to the mobile upon its initial request, the mobile would wait for a random number of time slots to pass before retransmitting its request for access. This was called random back-off.
- In GSM 04.60, which dealt with GPRS, there was a two-step test before the mobile gained access to the Packet Random Access Chanel (PRACH). The first step was to check whether the access class was barred, as above. The second step was a service-based persistence test. In particular the network transmitted a 4-bit persistence value for each of 4 differently defined radio priorities. The mobile would then conduct a persistence test by drawing a random value between 0 and 15 and compare this with the relevant transmitted threshold value. If the threshold (ie transmitted) value was less than or equal to the (mobile-generated) random number, then the access attempt would be allowed. If not, the attempt failed and the mobile would have to try again after a random time. It was possible to ensure that all attempts were successful by setting the threshold value to 0, or conversely to ensure that all attempts failed by setting the 4-bit value to correspond to 16.
IS-95
- This is a reference to TIS/EIA/IS-95 interim standard entitled "Mobile Station-Base Station Compatibility Standard for Dual-Mode Wideband Spread Spectrum Cellular System" published in July 1993. It was a proprietary system designed by Qualcomm, which was commercially released in the US and South Korea. Both experts agreed that the IS-95 system would be part of the skilled addressee's common general knowledge.
- IS-95 operated in 2 modes, one being analogue (which had a single access class barring mechanism) and the other being code division multiple access, or CDMA ...which involves all classes undergoing a persistence test in order to gain access). The argument at trial focussed on the latter, on the basis that UMTS was also going to be based on CDMA hence the CDMA aspects would be of more interest to the skilled addressee at the priority date. The relevant sections of IS-95 are 1.1.1, 2.3.5, 2.6.3.4, 6.6.3.1.1, 6.6.7.2, and 7.7.2.3.2.2.
- In summary there are 10 classes numbered 0 to 9, and six special classes (Access Overload Classes, or ACCOLC, 11 to 15). In IS-95, mobiles "are assigned one (or more) of sixteen overload classes. Access to the CDMA system can then be controlled on a per class basis by persistence values transmitted by the base station": see section 1.1.1 of IS-95 and Bishop I paragraph 8.12.
- When the mobile wants to access the Reverse Access Channel (called the R-ACH: the difference between this and the RACH is not material) it has to undergo a persistence test or "lottery". The network transmits parameters relating to this persistence test which vary depending on the type of class involved. For instance classes 0-9 are treated as a single group and share the same 6-bit value of PSIST. Conversely each of the special classes 10-15 has an individual 3-bit PSIST value transmitted by the network. The mobile uses the transmitted value of PSIST for the class to which it belongs in order to derive a value, P, which is compared to a random number RP generated by the mobile in order to see whether access is permitted. If not, it waits a random period until it is permitted to make another access attempt, or until it has run out of attempts.
- Again it was possible to ensure that all attempts for a mobile in a given class were unsuccessful, or conversely that all such attempts were successful, by ensuring that the value of PSIST for the relevant class was set to all 1's or all 0's, as the case may be. For instance if the transmitted PSIST value for classes 0-9 was 111111 then mobiles in all normal classes were barred.
- Because the PSIST value for the grouped normal classes could take any value from 0-63 (being 6 bits), and because the PSIST value for each special class could take any value from 0-7 (being 3 bits) there was a lot of flexibility built into the system. In particular the likely persistence delay could be varied over a large range for grouped classes 0-9, albeit that it applied equally to all of these classes; and the likely persistence delay could be varied over a smaller range for each of classes 10 to 15 separately.
- There is much more to IS-95 than this, but the further detail does not matter for present purposes.
The Patent
- Paragraph [0001] states as follows:
[0001] The invention takes as a starting point a method for ascertaining authorization for access to at least one telecommunications channel, and a subscriber station and a telecommunications system according to the independent claims.
- It then refers to various versions of the GSM standard and what they disclosed. For instance paragraph [0003] refers to a GSM method of authorising access depending on user classes and a persistence threshold value. See also paragraph [0005], which refers to a GSM lottery.
- Paragraph [0007] says this, my emphasis:
Advantages of the invention
[0007] The inventive mobile station, the inventive subscriber station, and the inventive telecommunications system with the features of the independent claims have, in contrast, the advantage that, with the information signals, access authorization data are transmitted to at least one subscriber station, that, upon receipt of the access authorization data in an evaluation unit of the at least one subscriber station, a check is carried out as to whether the access authorization data comprise an access threshold value, wherein the access threshold value is compared to a random number or a pseudo-random number, and that the right of access to a telecommunications channel is granted to the at least one subscriber station on the basis of the comparison result, preferably on the condition that the random number or a pseudo-random number is greater than or equal to the access threshold value. It is advantageous if in this manner a random distribution of the access authorization to this telecommunications channel is produced for one or more subscriber stations. This access control demands a minimum of transmission capacity for transmitting the information signals, since it is effected merely by transmitting the access threshold value.
- This paragraph [0007] was relied upon by Vodafone in connection with one of its arguments on construction, namely "access right". However in this paragraph the wording refers to "the right of access … is granted".
- Paragraph [0009] identifies a "particularly advantageous" feature. This is said to be the idea that using access class information for at least one prescribed user class permits subscriber stations (ie mobile phones) of that class to be authorised to use the telecommunications channel irrespective of the lottery. For instance this could be used for mobile phones belonging to emergency services such as the police or the fire brigade.
- Paragraphs [0010]-[0012] refer to advantages which are no longer claimed by the granted claims. As Floyd J noted in his judgment in the '268 case at [27], this is rather unhelpful.
- Paragraphs [0014]-[0036] include a fairly general section, followed by more detailed descriptions of a 10-bit embodiment (shown in Figures 3a, 3b) and a 13-bit embodiment (Figure 3c). The equivalent paragraphs and figures of the '268 patent were comprehensively reviewed by Floyd J in that case at [28]-[41].
- I need to say something about paragraph [0020], which is in the middle of this passage. That is as follows, my emphasis:
[0020] It is possible to prevent the RACH 30 from being overloaded by virtue of the network operator restricting, in a targeted manner, access to the RACH by the individual mobile stations 5, 10, 15, 20. In this case, access to the RACH can be permitted, for example, only for particular user classes of mobile stations on a temporarily or permanently privileged basis. In line with the described exemplary embodiments in figure 1, a first user class 35 is provided which comprises the first mobile station 5 and the second mobile station 10. In addition, a second user class 40 is provided which comprises the third mobile station 15 and the fourth mobile station 20. Provision may also be made for a separate user class to be provided for each mobile station, however. It could also be possible to provide user classes containing a different number of mobile stations. It is also possible to provide more than two mobile stations in one user class. The network operator can then enable access to the RACH for the individual mobile stations on the basis of their association with one of the two user classes 35, 40. This means that the two mobile stations 5, 10 in the first user class 35 are assigned equal rights for sending on the RACH. Similarly, the mobile stations 15, 20 in the second user class 40 are also assigned equal rights for sending on the RACH.
- This is the first reference to privilege in the Patent and I will return to it below. In the meantime I will summarise Floyd J's findings about the 13-bit embodiment in Figure 3c in order to assist the reader of this judgment.
- In this Figure 3c embodiment, the network is transmitting a bit pattern of 13 bits. These 13 bits include both an access threshold value S (for use in the lottery, if required) and user class information Z (which tells the mobile whether it can access the RACH irrespective of the access threshold value S). Each of these values consists of a number of bits: S3, S2, S1, S0 and Z3, Z2, Z1, Z0. The purpose of the exercise is so that the mobile can obtain access to the RACH in either of two ways.
1) If the associated access class bit for the user class to which the mobile belongs is 0, the mobile can access the RACH irrespective of the access threshold value. It does not have to do the lottery.
2) Conversely, if the relevant associated access class bit is 1, the mobile has to participate in the lottery using whatever access threshold value has been transmitted.
- In this Figure 3c embodiment, each user class must have an access class bit since otherwise the mobile would not be able to switch between the 2 routes of access.
- Figure 4 was not relevant in the '268 action, but it is by far the most important part of the '666 patent. It consists of a number of flowcharts (4a, b, c) which are explained at paragraph [0037]. There was no real dispute as to what this disclosed and I will use 2 diagrams prepared by Mr Bishop. First he amalgamated these 3 flowcharts into a single figure, as follows:
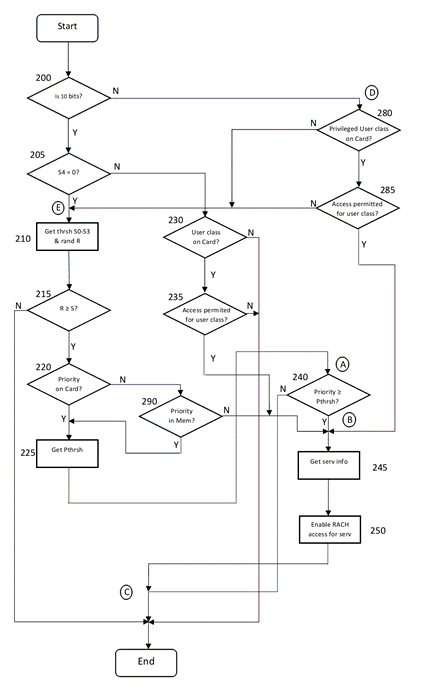
- The first decision diamond 200 asks whether the 10- or 13-bit process should be followed. If there are 13 bits, the system proceeds to diamond 280. At this point the system carries out two checks: first, is a user class stored on the mobile's access authorisation card (ie on its SIM card); secondly, if so is that user class "normally privileged" or "privileged"? This is described at p 21, lines 2-12 of the translation as follows, my emphasis:
At program point 280, the evaluation unit 60 has recognized that a bit pattern having a bit length of 13 bits has been received, and checks whether the access authorization card 75 stores an affiliation of the associated mobile station to a user class. In addition a check is carried out at program point 280 to determine whether the user class belongs to a first group of user classes or to a second group of user classes. The first group of user classes is also referred to as normally privileged below. The second group of user classes is also referred to as privileged hereafter.
In this diagram, Mr Bishop has amalgamated these 2 checks into a single question of "privileged user class on card?".
- The logic then proceeds as follows:
a) If the answer is yes (ie there is a privileged user class on the card), then the system goes to box 285 and asks whether access is permitted for that user class.
b) If the answer is again yes, then the system proceeds to boxes 245 and 250 whereby the privileged user whose access is permitted is given access to the RACH.
c) If the answer to diamond 280 is no, either because there is no user class stored on the card or because the user is normally privileged, then the system goes to point E, just above box 210. It then has to perform the lottery in order to see if it is permitted access.
d) Similarly if the answer to diamond 285 is no (ie the user is in a privileged class but access is not permitted for that particular privileged class), the same path is followed.
- The difference between "normally privileged" and "privileged" users is therefore that the "privileged" users can, if their access class is permitted, bypass the lottery. Even if the relevant access class of a privileged user is barred, that user can still access the RACH but only by participating in the lottery. However "normally privileged" users, and those who do not belong to any stored user class, always have to participate in the lottery in order to obtain access to the RACH. This means that the "normally privileged" classes do not actually enjoy any privileges, unless one counts the mere ability to access the RACH via the lottery to be a privilege. The terms "normally privileged" and "privileged" appear to be an artefact of the agreed translation of the Patent from the original German. The parties often referred to "the normals" and "the specials" respectively.
- The left side of the diagram (ie for 10-bit embodiments) does not refer to "privileged" users and is much the same as Figures 3a, b. For instance if S4=0 the system participates in the lottery, whereas if S4=1 then the system can bypass the lottery if so permitted.
- Mr Bishop had a second diagram which summarised the flow diagram above more concisely, as follows:

- Both experts accepted that in Figure 4, only privileged classes need to have an access class bit. This is because these are the only classes capable of bypassing the lottery. Dr Irvine also accepted that if one did want the flexibility of making any normally privileged class into a privileged class then that normally privileged class also needed to have an access class bit.
- Finally paragraph [0038] provided as follows, my emphasis:
[0038] The information signals are transmitted from the base station 100 to the mobile station 5, 10, 15, 20 at prescribed times, preferably at regular intervals. The network operator can, in line with the method described, permit or block access to the RACH for the individual mobile stations 5, 10, 15, 20 on the basis of the volume of message traffic in a telecommunications network and hence on the basis of an expected utilization level of the RACH 30. Since the volume of message traffic in the telecommunications network varies over time, the expected utilization level for the RACH 30 also changes over time, so that the various mobile stations 5, 10, 15, 20 are, in general, granted access to the RACH at different times using correspondingly altered bit pattern configuration.
- That brings me to the claims. Most of the arguments on construction revolved around unconditional claims 1, 3, and 13, and conditional claim 1. I set out the three unconditional claims below, with my emphasis.
- Unconditional claim 1:
1. Method for ascertaining an authorization for access to at least one telecommunication channel (30) of a telecommunication network by a subscriber station (5, 10, 15, 20),
wherein information signals sent by a base station (100) with access threshold value and access class information as access authorization data (55) are received by a transmission/reception unit (65) of the subscriber station (5, 10, 15, 20)
characterized in that
an evaluation unit (60) of the subscriber station (5, 10, 15, 20) has a check (280) performed in it to determine whether an access authorization card (75) of the subscriber station (5, 10, 15, 20) stores an association between the subscriber station (5, 10, 15, 20) and a privileged user class (35, 40),
if this is the case, then the evaluation unit (60) takes the access class information (Z0, Z1, Z2, Z3) as a basis for checking (285) whether the privileged user class (35, 40) ascertained for the subscriber station (5, 10, 15, 20) is authorized for access to the at least one telecommunication channel (30) irrespective of an access threshold value evaluation, if this is not the case or if the access authorization card (75) stores no association with a privileged user class (35, 40), then the evaluation unit (60) performs the access threshold value evaluation with the following steps:
(i) ascertains an access threshold value (S) from the access authorization data (55),
(ii) draws a random or pseudo-random number (R),
(iii)compares the access threshold value (S) with the random or pseudo-random number (R),
and
(iv) allocates an access right for the at least one telecommunication channel (30) to the subscriber station (5, 10, 15, 20) on the basis of the comparison result.
- Dr Irvine identified the key inventive concept of this claim as follows:
"In my opinion, the key inventive concept of claim 1 of EP666 is the combination of two different access regimes into one system: a bypass mechanism available to a group of privileged users only; and a threshold evaluation for those users not granted access via this bypass mechanism. The proportion of privileged users that are granted bypass access can be changed dynamically by way of the access class information broadcast by the network, and the proportion of the remaining users who will successfully gain access using the threshold evaluation can be controlled by way of the access threshold value broadcast by the network. This system combines the flexibility of a threshold with a bypass mechanism so that high priority mobiles in privileged user classes can gain direct access to RACH and escape the constraint of the threshold, all with limited signalling overhead."
- Vodafone agreed with this, so to that extent it is common ground. However I remind myself that the key inventive concept of the claim is not the same as the claim. Its importance is more in relation to, eg infringement under the doctrine of equivalents and inventive step.
- Unconditional claim 3 is as follows:
3. Method according to Claim 1 or 2, wherein the access class information (Z0, Z1, Z2, Z3) has access class bits (Z0, Z1, Z2, Z3) with each access class bit corresponding to a user class and indicating whether the user class to which the bit corresponds is authorized for access to the at least one telecommunication channel irrespective of an access threshold value evaluation.
- Unconditional claim 13 is as follows:
13. Telecommunication system having a telecommunication network that is in the form of a mobile radio network and that provides at least one telecommunication channel (30), at least one base station (100) that is set up to send information signals with access threshold value and access class information as access authorization data (55), and at least one subscriber station (5, 10, 15, 20) according to Claim 12 or Claim 12a.
- The parties' written submissions contained references to unconditional claims 2, 3a, 12, 12a, and 13a. There was a little oral argument on claim 3a but otherwise the parties appeared content to assume that these claims stood or fell with the ones which were argued. I shall assume likewise.
Construction
- It was not suggested that any of the terms in the Patent, or any of the claims, were technical terms or terms of art. In those circumstances construction is a matter for the Court, not for witnesses: see eg STEP v Emson [1993] RPC 513. Vodafone spent considerable time cross-examining Dr Irvine on what he thought the Patent meant, but Dr Irvine is not a lawyer and I did not find that exercise useful. Nor did I find Mr Bishop's extensive evidence on the same topic helpful either, for the same reason.
- Furthermore construction is done without reference to the alleged infringement. At most the nature of the infringement allows the court to concentrate on the important points: see Pumfrey J in Nokia v Interdigital [2007] EWHC 3077 (Pat) at [25].
- It was not disputed that I should adopt a purposive construction when considering the claims of the Patent, as I am doing now. I will then apply the doctrine of equivalents later, when considering infringement. See Eli Lilly & Company v. Actavis [2017] UKSC 48 at [54], [66] and Icescape Limited v. Ice-World Intl BV & ors [2018] EWCA Civ 2219 at [58]-[66], [95]-[96].
The unconditional claims
- The contentious issues of construction of the unconditional claims are:
a) "access right" (claim 1)
b) "routes through the claim" (claim 1)
c) "mutual exclusivity of 'privileged' and 'normally privileged'" (claim 1)
d) "each access class bit corresponding to a user class …" etc (claim 3)
e) "at least one base station that is set up to send information signals with access threshold value and access class information as access authorization data" (claim 13)
- I will deal with them separately because this is how they were argued, but in my judgment there is force in IPCom's submission that Vodafone spent rather longer on the meaning of individual words and phrases than on considering the relevant claims as a whole.
Access right
- The term "access right" appears towards the end of unconditional claim 1, in the context of performing the lottery. The specific issue is whether this claim 1 requires an actual right of access to the RACH, as Vodafone submits, or whether the "access right" allocated can be either yes or no, as IPCom submits. The dispute arises because Vodafone believes it makes a difference to infringement. In my view IPCom is right for the following reasons.
- First, claim 1 is to a method "for ascertaining an authorization for access …". It does not refer to "granting" an authorization for access, unlike paragraph [0007] of the Patent. Secondly, not everyone participating in the lottery is going to win. On the contrary there will always be losers (unless the lottery is rigged so that everyone wins, but even then the lottery is still performed). One either has to say that the allocation step is not performed at all for the lottery losers; or that the allocation step is always performed but sometimes the right is granted and sometimes it is denied depending on the lottery result. The latter view is consistent with the description of the method as being one for "ascertaining" an authorization for access. Thirdly paragraph [0038] says that the method described (ie in paragraph [0037]) can "permit or block access to the RACH for the individual mobile stations…". Fourthly there is no gap in the scope of protection since the actual access to the telecommunication channel is still claimed elsewhere: see eg unconditional claim 3a.
- Vodafone drew my attention to Floyd J's judgment in the '268 trial at [46]-[52]. However this is dealing with a different point, which is whether the privileged users are permitted to access the RACH without doing a lottery. The wording is different too. I do not rely on this.
"Routes through the claim"
- Vodafone's argument is that there are 3 routes to access in unconditional claim 1, and that "a system that does not provide that full series of claimed routes does not fall within the claim". It submits that this point is relevant to each of infringement, added matter, and inventive step. The 3 routes are said to be: privileged direct access, non-privileged lottery access; and privileged lottery access (for privileged users in a barred class who have to undergo the lottery). In support of this Vodafone relies on all the words between "checking" and "comparison result" in claim 1.
- IPCom disputes that this is an argument of construction at all. In particular IPCom submits that it is wrong in principle to construe a claim by the number of ways in which it can be infringed. I agree with that approach in principle. However I do agree with Vodafone up to a point. In particular I agree that the claim refers to these 3 different routes to access but as will be seen I do not agree with the next steps in Vodafone's arguments based thereon.
Mutual exclusivity of 'privileged' and 'normally privileged'
- The issue here is whether privileged and normally privileged users are mutually exclusive classes. It is said by Vodafone to go to each of infringement, added matter, and inventive step.
- I agree that these are mutually exclusive classes in terms of how unconditional claim 1 works. Privileged users either bypass the lottery or participate if their user class is barred, whereas normally privileged users always participate in the lottery. I see no reason why, in the real world, a given user could not belong to both of these mutually exclusive classes if his or her SIM card was set up in that way but that does not mean that the classes themselves cease to be mutually exclusive.
Each access class bit corresponding to a user class
- This arises here on unconditional claim 3, and on conditional claim 1 (among others). The issue is whether these claims require that every user class has an access class bit transmitted, as Vodafone submits, or merely the privileged classes, as IPCom submits.
- Vodafone's argument is partly linguistic and partly technical.
a) The linguistic argument is that the relevant claims refer variously to "each access class bit corresponding to a user class", and "wherein each access class bit represents one user class and wherein each of the user classes is assigned one access class bit". Thus the references are simply to user classes, not to privileged user classes.
b) The technical argument is that one could never convert a normally privileged user class into a privileged user class unless each of the normally privileged user classes had its own access class bit (much of which is common ground) Vodafone then submitted that this was what paragraph [0007] was talking about. In particular, Vodafone submitted that paragraph [0007] refers eg to changing a normally privileged user class (eg, everyone whose mobile phone number ends with the digit 1) into a privileged user class which is able to bypass the lottery. The ability to do so was said to be important in order to achieve a dynamic control of access.
- IPCom's response was as follows.
a) In the relevant claims, the term "user class" is used as a generic term when it was unnecessary or impossible to distinguish between normally privileged and privileged classes but not as a collective term for both.
b) In any event, the method only uses access class information, and hence the access class bits, in respect of the privileged user classes. If all classes were understood to have access class bits then the whole distinction of privileged and normally privileged user classes fell away.
- I agree with IPCom, for the reasons it gives. The wording of paragraph [0020] of the Patent is not very clear but I consider that this is simply saying a mobile station can be temporarily or permanently assigned to a privileged class. In other words, the word "temporary" refers to the particular mobile station, not to the whole user class of which that mobile forms part.
- The alternative view, ie that one can temporarily turn a whole normally privileged user class into a privileged user class, makes more linguistic sense but no technical sense. I can see no reason why one would temporarily make everyone whose telephone number ended in a 1 (ie 10% of the total number of system users, which will be a large number) into a privileged user able to bypass the lottery (a category which was only ever intended to cover a very limited number of high priority users). This runs contrary to the whole idea of having a limited number of privileged users. Furthermore I agree that it would be inefficient routinely to transmit extra bits relating to a normally privileged user class just on the off-chance that that this user class might one day be temporarily transformed into one which is privileged.
"Set up to send"
- The full integer refers to "at least one base station that is set up to send information signals with access threshold value and access class information as access authorization data". The dispute was as to what was meant by "set up to send" in this context.
- This is not the first case in which the Court has had to determine the meaning of a similar phrase. It has arisen in a number of previous decisions where (typically) a computer is programmed to carry out a particular task, and the claim language refers to apparatus which is "for", or "suitable for", carrying out that task. The issue then is whether the claim is satisfied (eg) by a general purpose computer which could be so programmed, or only by a computer which is in fact so programmed.
- For instance similar issues arose in each of Qualcomm v Nokia [2008] EWHC 329 (Pat), Floyd J, where the relevant word was "for"; Rovi Solutions v Virgin Media [2014] EWHC 1559 (Pat), Mann J, another case about "for"; and Philips v Nintendo [2014] EWHC 1959 (Pat), Birss J, where the claim included "apparatus operable to" and also processing means/a processor which was "arranged to". My attention was also directed to the EPO Guidelines considered by Birss J in Philips. I do not need to set these authorities out at length because the parties agreed what they established, as follows:
a) One must be cautious of any principle which is said to codify the meaning of words: see Philips at [102], citing Qualcomm.
b) The EPO generally takes claim language of the means plus function to be read as means suitable for carrying out the function, save where the function is to be carried out by a computer. In that case the features are interpreted as means "adapted to" carry out the relevant function rather than merely being suitable. See EPO Guidelines, F-IV, paragraph 4.13.2, November 2018 edition, headed "Interpretation of means-plus-function features".
c) Mann J's approach in Rovi was different. He held that a computer was not "suitable for" the processes in question without appropriate programming: see Rovi at [132].
d) The EPO approach and Mann J's approach are slightly different in form but it is doubtful whether they differ in substance: see Philips at [103].
e) A claim will still be infringed if all that is required is to supply power. Thus an apparatus for toasting bread infringes whether connected to the mains or not: see Qualcomm at [73]-[74], Philips at [104]. However if the apparatus has to undergo physical modification before it can be used for the relevant purpose, rather than merely being supplied with power, then prima facie it is not suitable for such use and does not infringe: ibid.
- Vodafone submitted that "set up to send" meant there was appropriate programming in the base station to send the relevant signals, or that the base station was adapted or configured for such purpose. IPCom agreed, and so do I. I interpret "set up to send" accordingly.
The conditional claims
- The final issue of construction arises on the conditional claims, but it is linked to an added matter argument in relation to the unconditional claims. It was referred to variously as the "two step check" or the "classless users" argument. Conditional claim 1 is in Appendix 1. I have presented it in a different format to the parties and have emphasised some sections with underlining.
- The issue here is whether conditionally amended claim 1 requires a specific two-stage checking process: first to see if a user class is stored on the mobile's SIM card; secondly, if so is that user class "normally privileged" or "privileged". I agree. This is apparent from the wording introduced by IPCom in order to meet the added matter objection to unconditional claim 1. See for instance "…checked whether an association of the subscriber station (5, 10, 15, 20) to a user class (35, 40) is stored on the access authorization card (75) and whether the user class is a normally privileged user class or a privileged user class…".
- In Mr Bishop's first diagram these 2 tests are rolled up into a single diamond box 280, but they are shown separately in his second figure. Whilst I must be careful to avoid construing the claim by reference to these figures, particularly the second, what they emphasise is that the end result is the same. I consider the consequences of this below.
Allowability of the amendments
- Vodafone objected to both the unconditional and the conditional amendments. Originally Vodafone objected on grounds of lack of clarity, added matter, and extension of protection but in closing it accepted that its arguments on lack of clarity would not succeed if its arguments on added matter did not. That was a realistic concession for which I am grateful.
- Both sets of amendments were put before the Comptroller who had no objection to either: see his letters of 25 July 2019 and 8 November 2019. It is right to note that the Comptroller was only looking to see if the amendments were allowable in themselves, whereas Vodafone's position was that the problems were contained in the Patent as granted. Vodafone also pointed out that at least some of its added matter arguments had succeeded before the EPO in the oral proceedings, whereas IPCom countered that Vodafone had lost before the EPO on extension of protection. In any event I have to form my own view.
Added matter
Legal context
- There was no dispute as to the law under 72(1)(d) of the Patents Act 1977/Article 123(2) EPC, which is by now very well known and which was recently summarised by Arnold J in Conversant v Huawei [2019] EWHC 1687 (Pat). In short matter will have been added to a patent by way of amendment unless the material in question would be derived by the skilled person directly and unambiguously, using common general knowledge, from the application for the patent as filed.
- See also AP Racing v Alcon Components [2014] EWCA Civ 40 at [9]:
9. In the end the question is the simple one posed by Jacob J. (as he then was) in Richardson-Vick Inc's Patent [1995] R.P.C. 568 at p.576 (approved by him as Jacob L.J. in Vector Corp v Glatt Air Techniques Ltd [2007] EWCA Civ 805, [2008] RPC 10 at [4]):
"I think the test of added matter is whether a skilled man would, upon looking at the amended specification, learn anything about the invention which he could not learn from the unamended specification."
- In many cases, including this one, there is argument about whether something is an "intermediate generalisation". This a sub-species of added matter which "occurs when a feature is taken from a specific embodiment, stripped of its context and then introduced into the claim in circumstances where it would not be apparent to the skilled person that it has any general applicability to the invention": see Kitchin LJ in Nokia v IPCom [2012] EWCA Civ 567 at [56]. However Kitchin LJ concluded his discussion of intermediate generalisation at [60] as follows:
60. Ultimately the key question is once again whether the amendment presents the skilled person with new information about the invention which is not directly and unambiguously apparent from the original disclosure. If it does then the amendment is not permissible.
- Vodafone had 3 arguments which it said were freestanding points of added matter, and 4 arguments which it said were "squeezes" on infringement. The former type of arguments have no broader significance to the case except for forcing IPCom to rely on the conditional claims (insofar as the problem arises in the unconditional claims but has been solved in the conditional claims).
- IPCom dispute that added matter arguments gave rise to any squeeze on infringement, citing Arnold J in Conversant at [222] as follows, my emphasis:
222. The Defendants add that the real vice was the amendment of the claim during prosecution to require (and hence disclose) a check to determine whether the MAC is transmitting data packets in a current TTI which was not disclosed in the Application, and that this is not cured by the amendment. (The Defendants also argue that the situation is compounded by Conversant's equivalence argument, which dilutes (the Defendants go so far as to say as to say "erases") the new limitation in integer C. In my judgment, however, this argument is misconceived, since it is an argument about the scope of protection, and not about disclosure. Infringement by equivalence cannot give rise to an added matter objection.)
- Vodafone had no argument to the contrary, and I respectfully agree with Arnold J. Added matter all turns on what is directly and unambiguously disclosed in the original application whereas infringement by equivalence is a different concept. I will nevertheless consider the alleged squeeze arguments briefly.
- Vodafone argued that the fact that the Patent was a divisional should be taken into account when assessing added matter. I do not see that this makes any difference to the relevant legal test.
Analysis
RACH
- Vodafone submitted that Figure 4 and its description only disclosed a method of gaining an access right to the RACH, but the unconditional claim referred generally to "at least one telecommunication channel" rather than just the RACH.
- IPCom pointed out that paragraph [0001] of the application referred to "a telecommunications channel" and the word RACH was not introduced until paragraph [0014] of the application when it was given "by way of example". It submitted that the whole application was directed to systems which used a RACH and that the concept of a RACH was common general knowledge in any event. Finally IPCom submitted that Vodafone had failed to identify what new information about the invention was actually disclosed, as compared to the original disclosure.
- I agree with IPCom that in this respect there is no additional disclosure about the invention. Although Figure 4 only addresses the RACH, the mere fact that the claim uses more general language than Figure 4 does not necessarily mean there is any added matter: it simply means that the scope of the claim is broader.
Single bit pattern
- Vodafone submitted that the term "access authorisation data" was an impermissible generalisation because the only access authorisation data contemplated in Figure 4, or indeed any of the specific embodiments of the application, was a single bit pattern. Vodafone also pointed out that unconditional claim 2 was specific to a bit pattern, and suggested this meant that IPCom implicitly accepted the criticism.
- IPCom submitted that this was effectively the same argument as failed in the '268 litigation at first instance and on appeal, even though Vodafone was advancing the argument in a different way (namely as an intermediate generalisation, and in relation to Figure 4 rather than Figure 3c, and in the context of LTE rather than UMTS). In any event IPCom submitted that the point failed anyway because Vodafone had again failed to identify what new information about the invention was actually disclosed, as compared to the original disclosure.
- Whether or not this is the same argument as in the previous case, I accept the second part of IPCom's submission. No matter has been added.
Two step check/normally privileged
- I have dealt with this topic above in relation to construction. Vodafone submits that the application only disclosed a 2-step check, pointing to the equivalent wording in the application of the passage which I highlighted at paragraph [55] above. Vodafone added that in the application it was necessary to have 2 steps because otherwise it was unclear how users without a class would be treated. Vodafone therefore submitted that matter has been added because unconditional claim 1 discloses for the first time that there need not be 2 checks (and also fails to explain how to treat users without a class).
- IPCom responded by pointing to the diagram in Figure 4c which shows a single box 280, to Mr Bishop's first diagram, and submitted that the only important distinction is between privileged users and everybody else.
- I agree with Vodafone that the application only disclosed a 2-step check whereas unconditional claim 1 not merely claims, but positively discloses, a single combined check. Since the test for added matter is a strict one, similar to the test for novelty, it follows that matter has been added. It is in this respect an impermissible intermediate generalisation, although this is simply saying that it adds matter in a particular way. IPCom's response elides the difference between disclosure (is a single step check actually disclosed in the application) and obviousness (is there any practical difference between a single step check and a two step check where both lead to the same end result; alternatively, is there any need specifically to check whether the mobile falls into a user class in circumstances where all real mobiles do).
Each user class has a corresponding access class bit
- I have already dealt with this topic in relation to construction of unconditional claim 3. It was relied upon as a squeeze on infringement, which as I have said is wrong in principle. However the argument fails anyway.
- Vodafone submitted that the relevant words were actually derived from the Figure 3 embodiments, not from Figure 4. Furthermore it submitted that if one wanted the flexibility of being able to turn a normally privileged user class into a privileged user class, that normally privileged user class needs its own access class bit. The difficult part of Vodafone's argument was the last step, ie identifying what new information about the invention was disclosed by unconditional claim 3 which was not directly and unambiguously apparent from the original disclosure.
- IPCom did not dispute that the relevant words had been derived from Figure 3 but submitted that there was no disclosure either in the original application or in unconditional claim 3 that any user class other than a privileged user might have its own access class bit. Hence the disclosure was the same and no matter had been added. I agree.
"Access right"; "set up to send"; scope of privileged user class
- I have already discussed these 3 topics in relation to construction but Vodafone ran essentially all the same points as squeezes in relation to infringement as well (albeit with rather less enthusiasm than the 4 points mentioned above). As I have said above this is wrong in principle but in any event these attacks all failed. In each case Vodafone failed to identify new information about the invention disclosed by the relevant claim which was not directly and unambiguously apparent from the original disclosure.
Squeeze arguments on conditional claims
- Although IPCom only introduced new wording into its unconditional claims in order to deal with what Vodafone (along with the EPO) had said was added matter in these unconditional claims, Vodafone nevertheless argued that the wording which it had thereby forced IPCom to introduce actually added yet more matter. In particular Vodafone had 4 such arguments, all of which it said were squeezes on infringement, but I have already rejected the premise of any squeeze between added matter and infringement. In any event I have considered the substance of these further arguments (each user class has a corresponding access bit, two step check, etc) elsewhere.
Conclusion on added matter
- I have only found for Vodafone on one of its added matter arguments. This still means that unconditional claim 1 is bad for added matter as a whole, as are all claims dependent thereon. That in turn means I need to consider the conditional claims. Furthermore, since IPCom did not have a claim set which only addressed this issue then the practical effect is the same as if Vodafone had won on, eg, the RACH and single bit pattern points as well.
- I appreciate that I have differed from the EPO first instance decision. Specifically Vodafone succeeded before the EPO with each of the first 4 added matter attacks considered above, although not with any of the others. However this is because I have formed my own independent view. In any event such EPO decision is likely to be the subject of appeal, which is only possible once the detailed reasons are given.
Extension of protection
- This objection applies to amendments sought post-grant during the present proceedings: see ss 75, 76(3)(b) of the Patents Act 1977. In particular the latter is as follows:
76. — (3) No amendment of the specification of a patent shall be allowed under section 27(1), 73 or 75 if it;
[…]
(b) extends the protection conferred by the patent.
- Vodafone submitted, and I agree, that it only needs to show that there has been such an extension by reference to a hypothetical example which may not be a real one. I agree, but the example does at least have to be a possible one.
- Vodafone's argument here was a variant of its "routes through the claim" argument. In particular it submitted that unconditional claim 1 required all non-privileged users (and barred privileged users, not relevant to this argument) to do the lottery. However conditional claim 1 now specifies that the non-privileged users have that status "because" they are either normally privileged users or users with no class: see lines 27-29 of conditional claim 1. So, the argument goes, unconditional claim 1 provided an exhaustive list of those who had to do the lottery whereas conditional claim 1 now provides a non-exhaustive list, and hence the scope of the claim has been extended.
- I reject this argument. There only ever were 2 types of non-privileged users, namely the normally privileged users and users with no class. That is still the position after amendment. Vodafone did not identify any other possible classes.
- Vodafone did put forward a fictional example which they said showed that the scope of protection had been extended. This was a notional class 16 user "that is not Privileged and not required to do the lottery". But no reason was given as to why the user in the fictional example was not required to do the lottery and I do not consider the example to be a possible one. I reject this argument too.
- I have therefore reached the same conclusion as both the EPO and the UKIPO on this point.
Obviousness over the prior art
Legal context
- The Supreme Court recently considered the approach to an allegation of obviousness in Actavis v ICOS [2019] UKSC 15. In Allergan v Aspire Pharma [2019] EWHC 1085 (Pat) Arnold J distilled 5 general points from Actavis at [96]-[102]. These are not controversial and I will not set them all out here. One point which is worth noting is that Lord Hodge, writing for a unanimous Supreme Court, endorsed the structured approach of Windsurfing/Pozzoli as an aid to avoiding the dangers of hindsight whilst making it clear that this approach is not mandatory: see Actavis at [60], [93] and Allergan at [97].
- Actavis also reinforced other case law warning against the use of hindsight, at [72].
72. Eighthly, the courts have repeatedly emphasised that one must not use hindsight, which includes knowledge of the invention, in addressing the statutory question of obviousness. That is expressly stated in the fourth of the Windsurfing/Pozzoli questions. Where the pattern of the research programme which the notional skilled person would undertake can clearly be foreseen, it may be legitimate to take a step by step analysis. In Gedeon Richter plc v Bayer Schering Pharma AG [2011] EWHC 583 (Pat); [2011] Bus LR D153, Floyd J stated (para 114):
"I think that the guiding principle must be that one has to look at each putative step which the skilled person is required to take and decide whether it was obvious. Even then one has to step back and ask an overall question as to whether the step by step analysis, performed after the event, may not in fact prove to be unrealistic or driven by hindsight."
The obvious danger of a step by step analysis is that the combination of steps by which the inventor arrived at his invention is ascertained by hindsight knowledge of a successful invention. Lord Diplock warned against this in Technograph Printed Circuits Ltd v Mills & Rockley (Electronics) Ltd [1972] RPC 346, 362, a warning which judges have reiterated in later cases. I am not persuaded by Mr Speck's suggestion that Technograph is concerned only with a case in which a step by step approach was constructed by counsel on cross-examination in the absence of evidence of routine steps of research. The case contains a wider warning against the use of hindsight and has been interpreted as doing so. I agree with Birss J's analysis in Hospira UK Ltd v Genentech Inc [2014] EWHC 3857 (Pat), para 240, where he stated:
"The particular point made in Technograph was that it was wrong to find an invention was obvious if it was only arrived at after a series of steps which involve the cumulative application of hindsight. In some circumstances success at each step in a chain is a necessary predicate for the next one and it is only the hindsight knowledge of the invention as the target which could motivate a skilled person to take each step without knowledge about the next one. In a situation like that, Technograph is important."
But the Technograph warning has no bearing in a case in which the steps which the notional skilled person would take can readily be ascertained without the taint of hindsight."
- I also remind myself of the importance, when considering an allegation of obviousness based upon the common general knowledge alone, of avoiding hindsight: see Nokia v IPCom [2012] EWCA Civ 567 at [128]-[129], per Kitchin LJ, with whom Etherton and Laws LJJ agreed. The danger is that such an attack is favoured by parties attacking the patent "because the starting point is not obviously encumbered with inconvenient details of the kind found in documentary disclosures, such as misleading directions or distracting context": :see [129], citing Floyd J in Ratiopharm v Napp [2008] EWHC 3070 (Pat) at [158].
Analysis
- When I first read into the case, it seemed to me that Vodafone was relying on 3, or perhaps 5, classical obviousness attacks: see the Re-Re-Re-Amended Grounds of Invalidity dated 11th November 2019. Vodafone disclaimed any case based on the common general knowledge alone: see ibid at footnote 1.
- This also appeared to be the basis on which Vodafone instructed Mr Bishop: see his first report at paragraphs [2.1(f)] to [(h)], [3.1]-[3.2]. However Vodafone only ever adduced evidence from Mr Bishop in support of one attack, namely that based on a combination of GSM/GPRS and IS-95.
- One might have thought that Vodafone's argument would proceed on the basis of how to improve IS-95, but it did not. On the contrary Mr Bishop's approach was to start with access control features extracted from the context of GSM/GPRS (ie 2.5G), in the context of developing UMTS (ie 3G), and using (or rather, modifying) various parts of IS-95.
- More particularly Mr Bishop's approach to unconditional claim 1 involved a number of steps. IPCom summarised them as follows:
Step 1: The skilled person interested in developing UMTS chooses to look at the IS-95 system for inspiration regarding RACH control.
Step 2: The skilled person wants the UMTS system to be interoperable with GSM/GPRS to make it easier to have a compatible SIM.
Step 3: The skilled person is not interested in considering, or had already rejected, looking at GSM/GPRS for anything else from its existing RACH access system.
Step 4: The skilled person would, however, retain the access classes from GSM/GPRS.
Step 5: The skilled person decides how to apply the IS-95 persistence test to the GSM/GPRS classes, grouping classes 0-9 together contrary to GSM/GPRS.
Step 6: Deciding to treat AC10 as a special access class as it is in IS-95 rather than as in GSM/GPRS.
Step 7: The skilled person treats classes 11-15 with the allocation of separate PSIST(N)s to retain the ability to give each of them prioritisation in different circumstances.
Step 8: The skilled person reduces the bit-allocation for classes 0-9 down from 6 bits to 4 bits for improved bit-efficiency.
Step 9: The skilled person decides to keep 3 bits for each of classes 10-15.
Step 10: The skilled person reduces the degree of control afforded by the separate PSIST(N) values for classes 10-15 to reduce transmission bits.
Step 11: The skilled person decides to group the special access classes together, and give them a single persistence value.
Step 12: To reintroduce the ability to control the special access classes individually and the ability to prioritise each of those classes separately, the skilled person introduces a GSM access barring facility for each of the special access classes.
Step 13: The skilled person now decides to throw away having separate thresholds for AC0-9 and 11-15, so that they all share the same threshold.[1]
Step 14: The skilled person finally decides to change the function of the GSM/GPRS barring bit to become a 'lottery bypass' flag.
- Vodafone submitted that the only real choices were at steps 5, 11, and 12. I do not agree. It seems to me that taking the idea of the GSM/GPRS access control, but nothing else, from the context of GSM/GPRS was a distinct choice, rather than a matter of simply putting GSM/GPRS in front of the skilled addressee (which I accept would not have involved any choice). The idea of combining the GSM/GPRS type of access control with that disclosed in IS-95 was another distinct choice. These ideas correspond to steps 1 and 3. Furthermore whilst I accept that steps 7-10 and 13-14 involve smaller steps, they are still steps.
- Mr Bishop himself did not accept that this sequence of steps was inventive. Indeed he did not accept that what IPCom described as his step 3 was an accurate description thereof, although I believe that IPCom was correct on this, and Mr Bishop did not suggest that IPCom's summary otherwise mischaracterised his approach. However I agree with IPCom that even if all the steps up to, say, step 9 were obvious, thereafter the exercise is unrealistic and driven by hindsight. It is a classic step by step approach of the type warned against in Technograph and subsequent cases.
- One might have thought that it would be possible to express Mr Bishop's argument in terms of a structured Pozzoli approach, but he did not do so. I asked Vodafone's legal representatives if they could produce an argument based on the Pozzoli approach and in closing they provided me with a document setting out their contentions in this respect. The first column referred to whether the features of unconditional claim 1 were disclosed in IS-95 in CDMA operation, the second column separately referred to whether such integers were disclosed in GSM/GPRS, and it contained various arguments as to how one might have gone from an integer contained in one column or the other to the claim by making various modifications to whatever was disclosed. Vodafone did not present any detailed arguments on this document, nor was it put to Dr Irvine either. If anything, it reinforces my conclusion that Vodafone's argument is based on hindsight.
- I reach the same conclusion by standing back and considering the matter more generally. The key inventive concept of the Patent involves the use of a bypass mechanism available to a group of privileged users only, and a threshold evaluation for those users not granted access via this bypass mechanism (and both of these can be changed/controlled dynamically, etc). But there is nothing in either GSM/GPRS or IS-95 which discloses or teaches anything about any bypass mechanism: this is a different sort of idea. For instance GSM/GPRS did have both access class bits and a persistence test, but that was a sequential barring mechanism not a bypass. Nor was Mr Bishop able to point to any prior art which even hinted at it.
- That is not the end of the matter. Vodafone submitted that regardless of Mr Bishop's evidence one could arrive at the claim purely on the basis of either 2, at most 3, items of common general knowledge alone. Both were run by Vodafone as squeeze arguments but I need to consider their impact on validity.
- The 2-step version is based on Vodafone's assertion that Dr Irvine made an important admission in his evidence, to the effect that the claim covered a privileged user of the claim who was associated with both a normal class (0-9) and a special class (11-15). It was then said to be common ground between the experts that the skilled person would take the following steps:
i) adopt the IS-95 approach of putting classes 0-9 together in a single large group, offered access by a persistence test;
ii) adopt GSM access barring for the special classes so that the network can signal (i) which of them just proceed to access the RACH (GSM access barring "0") and (ii) which are barred (GSM access barring "1").
- This argument does not succeed for a number of reasons. First, whilst Dr Irvine's views on technical matters were helpful his views on what the claim covers are irrelevant. Secondly I have already explained that the 2 classes themselves are mutually inconsistent. Thirdly, as IPCom pointed out Dr Irvine's views were expressed in the context of LTE, not in the context of the claim. Fourthly, it is another example of the type of argument based solely on common general knowledge which is unencumbered by detail and against which the Court has to be cautious. Fifthly it again involves hindsight. Sixthly this argument was never pleaded nor was it ever advanced in Mr Bishop's evidence. It first emerged in an opportunistic fashion in Vodafone's closing submissions and that approach is unfair to IPCom.
- The 3-step version essentially asserts that steps 5, 11, and 12 of Mr Bishop's 14 steps were the only steps necessary in order to come from an unidentified starting point in the claim: see Vodafone's closing at [443]. In my view this line of argument is a lawyer's one which was not advanced by Mr Bishop himself, nor was it suggested by any contemporaneous documents either. It is as unencumbered by detail as the 2-step version. I reject this as being another example of one which is influenced by hindsight.
- Vodafone's last throw of the dice was a suggestion, made for the first time at the end of its closing speech, to the effect that the invention was a mere collocation. This argument was not developed further, nor had it been explored in any of the extensive expert evidence, and I reject it.
- In reaching my conclusion I have been careful to consider only the evidence in this case, focussing particularly on that given by Vodafone's own expert. I have not relied on any of the following:
a) The decision of Floyd J in the '268 case, upheld by the Court of Appeal, that the patent in suit in that action (which is similar but not identical to '666) was inventive over the prior art considered therein.
b) Dr Irvine's evidence in this case that the Patent was inventive. I do not doubt that he honestly holds such views but I am concerned that he may have been setting the bar for inventive activity too low.
c) A document recording a presentation by the then patentee (Bosch) to the ETSI committee on RACH access, which was put to Mr Bishop in cross-examination. Whilst the document was interesting it did not seem to take matters further.
d) IPCom's argument that nobody in the industry suggested the changes which Vodafone now says were obvious even after many companies became involved in the development of IS-95. I do not place any weight on this because as Mr Bishop pointed out, that simply means that they did not want to alter IS-95 itself.
e) The EPO's decision to maintain the Patent on the basis of the conditional claims notwithstanding IS-95. The EPO Opposition Division's written reasons have not been made available but see the preliminary opinion of 17 January 2019 (which is relied upon by Vodafone in support of its added matter arguments) at section 4. As I have said, that decision is likely to be appealed.
- I have focussed on unconditional claim 1, as did the parties. No reasons were given as to why any other claim should be held to be obvious if this claim was upheld.
Essentiality
Legal context
- The law regarding declarations of essentiality is now well-established. In summary it means that a patent is essential to a standard if it is not possible on technical grounds to comply with that standard without infringing the patent: see the ETSI IPR policy, 3rd April 2019, in the definitions section at paragraph 15(6). The declarations which will be granted by the Court tend to follow the pattern of saying eg that "the importation, manufacture, [etc] of mobile telephones and/or infrastructure equipment compliant with [the ETSI standard] does not require infringement of [the patent in suit] such that [the said patent] is not essential IPR to [the standard]": see eg Nokia v Interdigital [2005] EWCA Civ 614. The precise wording of the declaration sought may of course vary.
- The more difficult area is where a patent is essential to a feature which is described in the relevant technical standard as an option. Since the feature is by definition optional to the standard, the patent cannot be "essential" to the standard on a conventional use of language. The present case highlights another possibility: what if the feature is optional to some people (eg a network operator) but essential to others (eg a handset manufacturer may need to ensure that its handsets can always work in accordance with this option, whether or not the option is actually used)? The common law has traditionally found a way through conceptual difficulties by focussing on the practical issues instead. I therefore turn to the practical issues in this case, starting with the relevant standard.
The relevant standard – 3GPP TS 36.331, version 12
- This is a very lengthy document, but I only need to refer to 2 sections. One is the definition of SystemInformationBlockType2 ("SIB2") at 6.3.1. That defines various parameters including ac-BarringForSpecialAC (a 5 bit string) and ac-BarringFactor (which can have a range of values from p00 to p95).
- More particularly it states as follows:
ac-BarringForSpecialAC
Access class barring for AC 11-15. The first/ leftmost bit is for AC 11, the second bit is for AC 12, and so on.
This allows the string to identify which special user classes from 11 to 15 are allowed to bypass the lottery.
ac-BarringFactor
If the random number drawn by the UE is lower than this value, access is allowed. Otherwise the access is barred. The values are interpreted in the range (0,1): p00 = 0, p05 = 0.05, p10 = 0.10,…, p95 = 0.95. Values other than p00 can only be set if all bits of the corresponding ac-BarringForSpecialAC are set to 0.
- First, note that the number following p is the lottery threshold. If the value is p05, then all random numbers below .05 (which means 5% of all random lottery attempts, or 1 in 20 thereof) will win the lottery. If the value is p00, then it is not possible to win the lottery since participants cannot generate a number which is lower than zero.
- Secondly, the last sentence provides that unless all of the special user classes are allowed to bypass the lottery, the threshold will be set at a level which means all lottery participants lose. The thinking appears to be that if any of the special user classes are barred, then nobody else should be allowed access either.
- The section dealing with the Access Barring Check, ie section 5.3.3.11, is as follows:
5.3.3.11 Access barring check
1> if timer T302 or "Tbarring" is running:
2> consider access to the cell as barred;
1> else if SystemInformationBlockType2 includes "AC barring parameter":
2> if the UE has one or more Access Classes, as stored on the USIM, with a value in the range 11..15, which is valid for the UE to use according to TS 22.011 [10] and TS 23.122 [11], and
NOTE: ACs 12, 13, 14 are only valid for use in the home country and ACs 11, 15 are only valid for use in the HPLMN/ EHPLMN.
2> for at least one of these valid Access Classes the corresponding bit in the ac-BarringForSpecialAC contained in "AC barring parameter" is set to zero:
3> consider access to the cell as not barred;
2> else:
3> draw a random number 'rand' uniformly distributed in the range: ≤ = rand < 1;
3> if 'rand' is lower than the value indicated by ac-BarringFactor included in "AC barring parameter":
4> consider access to the cell as not barred;
3> else:
4> consider access to the cell as barred;
1> else:
2> consider access to the cell as not barred;
1> if access to the cell is barred and both timers T302 and "Tbarring" are not running:
2> draw a random number 'rand' that is uniformly distributed in the range ≤ = rand < 1;
2> start timer "Tbarring" with the timer value calculated as follows, using the ac-BarringTime included in "AC barring parameter":
"Tbarring" = (0.7+ 0.6 * rand) * ac-BarringTime.
- The first 2 lines of code do not matter for present purposes and nor do the last 5 lines. The intermediate steps involve a series of questions which I will paraphrase as follows:
1) Does the SIB2 block include barring parameters? For present purposes I will focus on only ac-BarringForSpecialAC and ac-BarringFactor.
2) If yes,
a. Does the SIM card on the mobile have a valid access class between 11 and 15; and if yes
b. For at least one of those valid access classes on the SIM between 11 and 15, is the corresponding bit in the ac-BarringForSpecialAC set to 0?
c. If yes to both (a) and (b), consider access to the cell as not barred.
3) If the SIB2 block includes barring parameters and either 2(a) or 2(b) is not satisfied, do the lottery and compare the result to the value indicated by ac-BarringFactor. Winners are considered not barred and losers are considered barred.
4) If the SIB2 block does not include barring parameters, consider the cell as not barred.
- It will be seen that the fields ac-BarringForSpecialAC and ac-BarringFactor both need to be transmitted for this method to work. Otherwise the system does not know whether users in the special classes have an active bypass for the lottery, nor what the winning score in the lottery is. I have used the terms "considered not barred" and "considered barred" because that is what it says, and because Vodafone points out that the mobile does not actually gain access to the relevant telecommunications channel as a result of the process.
- Thirdly it was common ground that whether to operate access control at all within LTE was optional. My attention was drawn to a different LTE standard document (3GPP TS 22.011 version 12.3.0 release 12) which stated as follows:
"4 Access Control
4.1 Purpose
Under certain circumstances, it will be desirable to prevent UE users from making access attempts (including emergency call attempts) or responding to pages in specified areas of a PLMN. Such situations may arise during states of emergency, or where 1 of 2 or more co-located PLMNs has failed.
…
The use of these facilities allows the network operator to prevent overload of the access channel under critical conditions.
It is not intended that access control be used under normal operating conditions."
- Thus a network operator might choose to configure their network (eg as regards the number of base stations or the dimensions of each cell) so as to avoid the situation whereby any base station was overloaded with mobiles seeking access. Alternatively a network operator might just decide to put up with the overload situation as and when it happened. In both cases there would be no need to use access control. Mr Bradbury gave some other possibilities in his confidential witness statement at paragraph [31].
- Finally Vodafone has admitted for the purposes of these proceedings that it has been in possession of at least one handset which follows the LTE standard. The number of handsets which so comply is not relevant to liability.
Is it possible on technical grounds to comply with the standard without infringing the Patent?
Unconditional claim 1
- I first consider whether the parts of standard 36.331 which I have identified above read on to the wording of unconditional claim 1. In my view they do. Specifically:
a) The first step of the logic identified above refers to whether there are information signals sent by a base station with both types of information: access threshold value for the lottery, and access class information for the lucky classes.
b) Then the mobile phone checks whether its SIM card stores an association between the mobile and a privileged user class.
c) "If this is the case", ie there is such an association, then there is a check to see whether that privileged user class is authorised to bypass the lottery;
d) "If this is not the case" (ie this privileged class is not authorised), or if there is no stored association with a privileged user class, then the lottery is performed.
- Vodafone's arguments to the contrary were as follows:
1) First, that sending the relevant information signals was optional.
2) Secondly, that where p=00 there was no possibility of a lottery winner having an "access right" to the RACH.
3) Thirdly, that in LTE there were no access class bits for each user but only for privileged users.
4) Fourthly, that there was only 1 check in LTE (privileged users vs everyone else) whereas 2 checks were required.
- I agree with Vodafone's first point. Where the network operator decides not to send any barring parameters, the method of unconditional claim 1 is not being used at all. The same goes for conditional claim 1. However this goes back to the point about optionality I mentioned earlier. Since access control is optional in the standard then it cannot be essential to the standard in the normal use of language, but the patent can still be essential if and insofar as the network operator chooses to implement the option set out in section 5.3.3.11 of the standard.
- The second argument turns on what is meant by "access right" in the claim. I have decided this issue of construction against Vodafone, so I reject this as a defence to the declaration of essentiality sought. However it is worth saying a little more since some time was spent on it.
- Vodafone's starting position was that the invention was for a flexible system of operation with 2 adjustable dials, one for users able to bypass the lottery and the lottery dial for everyone else. Vodafone accepted that the situation where ac-BarringFactor was set at p05 (ie where the lottery is performed for everyone who participates, and 95% of lottery participants lose but 5% win) was within the claim. Vodafone also accepted that if ac-BarringFactor was set at p00 for a short period of time (eg at a football match) then the invention was still performed, because what it called the flexibility of the invention was thereby still retained. However Vodafone drew a distinction between the situation whereby ac-BarringFactor was set at p00 for (eg) half an hour, or 3 days, or 364 days of the year and the situation whereby it was permanently set at p00. In the latter situation the invention would, at some indeterminate time depending on what was meant by "permanently", cease to be operated.
- I reject this argument. First, it depends on a paraphrase of the claim rather than on the claim itself. Secondly, I do not accept that moving the notional dial from p05 to p00 makes any difference to whether the lottery is performed, or (as I have said) to the invention. It merely makes a difference to the possible outcomes. Thirdly it cannot possibly be right that whether or not unconditional claim 1 is infringed depends on some indeterminate time period.
- The third argument turns on an argument of construction which I have determined against Vodafone, so I reject it.
- I agree with Vodafone that unconditional claim 1 is bad for added matter because of the fourth point, but if I am wrong about that then unconditional claim 1 would have been infringed on the normal interpretation thereof.
Conditional claim 1
- Despite the additional length of conditional claim 1, most of the arguments were ones I have already considered and in my view there is only one additional issue. That is whether it is not possible on technical grounds to comply with the access control option in section 5.3.3.11 without infringing unconditional claim 1 insofar as Vodafone's fourth point ("2 checks") is concerned. I do not regard the "users with no stored class" point as being distinct from the "2 checks" point for this purpose.
- Vodafone submitted that conditional claim 1 was not infringed by the method set out in section 5.3.3.11 in the standard because of the "2 checks" point. The argument was that because conditional claim 1 required 2 checks, and section 5.3.3.11 only performs one check (omitting a separate check to see if there was a user class at all) then the method set out in this section was not infringed by conditional claim 1; and hence conditional claim 1 was not essential.
- IPCom disputed this on the basis that insofar as conditional claim 1 was not infringed on a normal construction by section 5.5.3.11 then it was still infringed on the doctrine of equivalents.
- I agree with Vodafone that conditional claim 1 is not infringed by the method set out in section 5.5.3.11 on its normal construction, for the reasons Vodafone gives. Hence I now consider infringement on the doctrine of equivalents.
- Actavis sets out 3 questions in relation to the doctrine of equivalents, which were re-stated by Kitchin LJ in Icescape (with whom Floyd and Longmore LJJ agreed) at [66(iii)] as follows:
"(a) Notwithstanding that it is not within the literal (that is to say, I interpolate, normal) meaning of the relevant claim(s) of the patent, does the variant achieve substantially the same result in substantially the same way as the invention, i.e. the inventive concept revealed by the patent?
(b) Would it be obvious to the person skilled in the art, reading the patent at the priority date, but knowing that the variant achieves substantially the same result as the invention, that it does so in substantially the same way as the invention?
(c) Would such a reader of the patent have concluded that the patentee nonetheless intended that strict compliance with the literal meaning of the relevant claim(s) of the patent was an essential requirement of the invention?"
- IPCom submitted, and Vodafone did not dispute, that the answers to the first two questions were "yes" and "yes" respectively. If I return to the agreed summary of the key inventive concept (see above) it will be seen that the number of checks is not material. Indeed Figure 4 itself rolls up the number of checks into a single decision diamond. In addition it was not disputed that in the real world every user will have a user class.
- Hence the key question is the last one. It did occur to me that (as with the first Actavis question) this should perhaps be understood as asking whether strict compliance with the "normal" meaning is required rather than with the "literal" meaning, but nothing turned on this and I will not consider that further. Instead Vodafone's argument was that because unconditional claim 1 to a single check had been found invalid for added matter, and as a result IPCom was forced to rely on an amended claim which referred to 2 checks, then IPCom was not permitted to argue that a method with a single check (ie as per paragraph 5.3.3.11) infringed the amended claim.
- I reject this argument. As IPCom pointed out, this is the same argument as was rejected by Arnold J in Conversant and which I have already discussed above. It muddles up the strict novelty-type test for added matter with the different legal test for infringement. It was also difficult, if not impossible, to reconcile this argument with the law that "An amendment of a specification of a patent … shall have effect and be deemed always to have had effect from the grant of the patent": see s 27(2) of the 1977 Act.
- It is worth considering what the consequences would be if Vodafone's argument were correct. For instance suppose there are 2 skilled addressees, one who has read the full prosecution file and the (final form of the) patent, and one who has merely read the patent itself. If the scope of protection depends on amendments made during prosecution then they might have different views of the scope of the invention. Indeed everyone would presumably always have to read the entire history of all amendments made during prosecution in order to see what the answer to the final Actavis question was, even though reviewing the prosecution file was discouraged in Actavis itself.
- No other reason was given as to why the final Actavis question should be answered "yes" and in my view the answer should be "no". I can see no reason why a reader could have concluded that a 2 step check would be required given the nature of the key inventive concept. I conclude that operating access control as per paragraph 5.3.3.11 infringes unconditional claim 1.
- It follows that in principle IPCom is entitled to the declaration of essentiality sought, but I will hear argument about the precise wording. I will also deal with the remaining claims which were argued.
Unconditional claim 3
- The only point here was the argument about whether each class requires its own access class bit, which I have resolved in favour of IPCom. Even if I were wrong about that on a normal construction of the claim, I would still have held that there was infringement under the doctrine of equivalents for similar reasons as set out above.
Unconditional claim 3a
- I have not set this out in full since the point is a short one. Vodafone's argument here was a variation on its "p00" argument. Vodafone relied on the sentence in the standard stating that "Values other than p00 can only be set if all bits of the corresponding ac-BarringForSpecialAC are set to 0." Thus if any given privileged user class is barred, then that particular user has to undergo the lottery and since ac-BarringFactor is set to p00 then that particular user will lose the lottery.
- I do not accept that this amounts to a defence to infringement of unconditional claim 3a any more than I have accepted that the p00 argument provides a defence to unconditional claim 1. My reasoning is the same.
Unconditional claim 13
- I will return to unconditional claim 13 in relation to the discussion of Vodafone's actual system since most of the argument was advanced in that particular context.
- For present purposes I accept that if the LTE network is in such a state that it merely needs power in order to operate access control as per section 5.3.3.11, then it is "set up to send" and hence acts done in relation to that network will infringe unconditional claim 13. Unconditional claim 13 is only "essential" when the network is in this state. Conversely if the LTE network requires some form of adaptation, configuration, or additional programming going beyond the mere supply of power then it is not "set up to send" and acts done in relation to it will not infringe unconditional claim 13.
Unconditional claim 13a, Conditional claims 6 and 7
- It was not disputed that these stood or fell with unconditional claim 13.
Arguments based on non-implementation of the standard
- Mr Bishop gave some evidence about how those implementing the standard would do so in the most efficient way possible. I accept this evidence but nothing turns on it since it was not suggested that any specific point on implementation (other than the fact that access control is optional) made a difference.
- Of course if the implementer decides to depart from the standard (eg deciding not to do the lottery at all when ac-BarringFactor is set to p00) then that is irrelevant to this part of the case since the implementation is no longer following the standard.
Infringement
- Since Vodafone has admitted that it has kept at least one handset complying with the standard, one might have thought that a finding of infringement would follow upon a finding of essentiality. In fact there were a number of additional issues, as follows:
a) Vodafone's Crown use defence in relation to some acts alleged to infringe;
b) Vodafone's defence that some of its use was de minimis.
c) Specific factual argument as to whether Vodafone's base stations were "set up to send" the relevant signals for purposes of unconditional claim 13.
d) S 60(2) infringement in relation to SIM cards.
e) Miscellaneous arguments relating to a kit of parts, and other matters.
- I also remind myself of IPCom's acceptance that acts done in relation to the fundamentally redesigned system do not infringe '666 when it is operating in 4G, hence all of above points relate to historical rather than current infringement.
- In order to deal with these arguments I need to set out details of the alleged infringements, some of which are said by Vodafone to be confidential. I am prepared to accept this is so up to a point, although my impression was that Vodafone's concerns in this respect were somewhat overblown. I have therefore set out what I consider to be genuinely confidential information in Confidential Appendix 2 but the rest of this judgment will be publicly available.
The Crown use defence
Legal context
- The Patents Act 1977 sets out the general scheme of Crown use at ss 55-59. Section 55 provides for the defence, including provision for compensation at 55(4); section 56 contains important provisions of interpretation; section 57A provides for a compensatory scheme additional to s 55(4); and section 59 makes special provision for Crown use during emergency. Most of the argument before me centred on the specific sections set out below, my emphasis.
"55.— Use of patented inventions for services of the Crown.
(1) Notwithstanding anything in this Act, any government department and any person authorised in writing by a government department may, for the services of the Crown and in accordance with this section, do any of the following acts in the United Kingdom in relation to a patented invention without the consent of the proprietor of the patent, that is to say—
(a) where the invention is a product, may—
(i) make, use, import or keep the product, or sell or offer to sell it where to do so would be incidental or ancillary to making, using, importing or keeping it; or
(ii) in any event, sell or offer to sell it for foreign defence purposes or for the production or supply of specified drugs and medicines, or dispose or offer to dispose of it (otherwise than by selling it) for any purpose whatever;
(b) where the invention is a process, may use it or do in relation to any product obtained directly by means of the process anything mentioned in paragraph (a) above;
…
and anything done by virtue of this subsection shall not amount to an infringement of the patent concerned.
(2) Any act done in relation to an invention by virtue of this section is in the following provisions of this section referred to as use of the invention; and "use" in relation to an invention, in sections 56 to 58 below shall be construed accordingly.
(3) So far as the invention has before its priority date been duly recorded by or tried by or on behalf of a government department or the United Kingdom Atomic Energy Authority otherwise than in consequence of a relevant communication made in confidence, any use of the invention by virtue of this section may be made free of any royalty or other payment to the proprietor.
(4) So far as the invention has not been so recorded or tried, any use of it made by virtue of this section at any time either;
(a) after the publication of the application for the patent for the invention; or
(b) without prejudice to paragraph (a) above, in consequence of a relevant communication made after the priority date of the invention otherwise than in confidence;
shall be made on such terms as may be agreed either before or after the use by the government department and the proprietor of the patent with the approval of the Treasury or as may in default of agreement be determined by the court on a reference under section 58 below.
…
(7) Where any use of an invention is made by or with the authority of a government department under this section, then, unless it appears to the department that it would be contrary to the public interest to do so, the department shall notify the proprietor of the patent as soon as practicable after the second of the following events, that is to say, the use is begun and the patent is granted, and furnish him with such information as to the extent of the use as he may from time to time require.
…
56.— Interpretation, etc., of provisions about Crown use.
(1) Any reference in section 55 above to a patented invention, in relation to any time, is a reference to an invention for which a patent has before that time been, or is subsequently, granted.
(2) In this Act, except so far as the context otherwise requires, "the services of the Crown" includes -
(a) the supply of anything for foreign defence purposes;
(b) the production or supply of specified drugs and medicines; and
(c) such purposes relating to the production or use of atomic energy or research into matters connected therewith as the Secretary of State thinks necessary or expedient;
and "use for the services of the Crown" shall be construed accordingly
…
59.— Special provisions as to Crown use during emergency.
(1) During any period of emergency within the meaning of this section the powers exercisable in relation to an invention by a government department or a person authorised by a government department under section 55 above shall include power to use the invention for any purpose which appears to the department necessary or expedient—
(a) for the efficient prosecution of any war in which Her Majesty may be engaged;
(b) for the maintenance of supplies and services essential to the life of the community;
(c) for securing a sufficiency of supplies and services essential to the well-being of the community;
(d) for promoting the productivity of industry, commerce and agriculture;
(e) for fostering and directing exports and reducing imports, or imports of any classes, from all or any countries and for redressing the balance of trade;
(f) generally for ensuring that the whole resources of the community are available for use, and are used, in a manner best calculated to serve the interests of the community; or
(g) for assisting the relief of suffering and the restoration and distribution of essential supplies and services in any country or territory outside the United Kingdom which is in grave distress as the result of war;
and any reference in this Act to the services of the Crown shall, as respects any period of emergency, include a reference to those purposes.
…
(3) In this section "period of emergency" means any period beginning with such date as may be declared by Order in Council to be the commencement, and ending with such date as may be so declared to be the termination, of a period of emergency for the purposes of this section.
(4) A draft of an Order under this section shall not be submitted to Her Majesty unless it has been laid before, and approved by resolution of, each House of Parliament."
- Both sides made submissions as to how the above provisions should be interpreted. However since this also involves the public interest it seemed to me that I would benefit from hearing the Comptroller's views. I therefore invited the parties to write to the Comptroller accordingly. As it happened, the Comptroller provided me with written submissions by email on 18 December 2019, after I had already provided the parties with a draft judgment and shortly before the hand-down planned for 20 December 2019. The Comptroller pointed out, and I accept, that his statutory role was independent from (and not representative of) any other arm of government which might have an interest in whether, on the facts of a particular case, Crown use had taken place and any consequences thereof. Even with that limitation I still found the Comptroller's observations helpful and I am grateful for them. I then allowed both sides to submit further written submissions in relation to some points made by the Comptroller which had not previously been discussed. These post-trial materials ended up running to 35 pages excluding authorities, which is almost double the total number of pages devoted to the same topic at trial. Finally I reconsidered this section of my judgment in the light of this additional material.
- I will start with the easier points. These are as follows.
1) There has to be evidence of authorisation in writing by a government department: see MMI Research v Cellxion [2009] EWHC 1533 (Pat).
2) The words "for services of the Crown" do not necessarily mean that the use has to benefit the Crown itself directly: see Pfizer v Minister of Health [1965] 2 WLR 387, HL, a case about use of patented drugs to treat NHS patients. The words also include use by members of Crown services (such as the armed services) in the course of their duties: see the speech of Lord Reid, with whom Lords Evershed and Upjohn agreed, at 392B-D.
Pfizer was a case on s 46 of the Patents Act 1949, but IPCom did not say it was irrelevant for that reason. IPCom merely submitted that Pfizer involved the production or supply of specified drugs and medicines, which is now expressly covered under s 56(2)(a). This is true but I do not see what turns on it.
3) In any event the concept of use for the Crown's own benefit is itself a wide one. For instance in Henry Brothers (Magherafelt) v Ministry of Defence [1999] RPC 442, CA, the Court of Appeal held, albeit obiter and in a case not involving Crown use (it was actually about s 36, ie co-ownership), that use of an invention relating to prefabricated blast-resistant building structures in a police station in Northern Ireland was use for the Crown's own benefit.
Does s 56(2) provide an exhaustive list of "for the services of the Crown"?
- The first of the more difficult points was whether the 3 examples given in s 56(2) provided an exhaustive list of what was meant by "for the services of the Crown" in peace time (ie outside an emergency). IPCom submitted this was so, and relied upon the closing words of s 56(2). Vodafone submitted to the contrary, relying on the words "including". In particular Vodafone submitted that the closing words did not mean that the 3 examples given were the only possible ones. The Comptroller agreed with Vodafone's position.
- I agree with Vodafone and the Comptroller. The word "includes" plainly indicates that the examples are intended to be non-exhaustive. The closing wording merely confirms that the words "use for the services of the Crown" are to be construed as covering, but not limited to, the examples given. I note this is the view of s 56(2) set out in the UKIPO's Manual of Patent Practice, 1 October 2019 at ss 55.04, 56.03; and in the CIPA Guide to the Patents Act, 56.04. In addition Terrell on the Law of Patents, 18th edition, submits at 25-10 that the specific use identified in Henry Brothers would also have been use "for the services of the Crown". I agree.
- I also agree with Vodafone and the Comptroller that s 59 does not expressly or impliedly limit s 56 to the 3 specific examples given. On the contrary s 59 provides a separate defence for a much broader list of acts including those which would not generally be regarded as being "use for the services of the Crown" even on the widest view of these words: see eg 59(b) to 59(f).
Implied authorisation
- The next more difficult point related to the concept of implied authorisation. It was not disputed that in principle an authorisation can be implied: see Aktiengelsellschaft für Aluminium Schweissung v. London Aluminium Co. Ltd. (No. 2) (1923) 40 RPC 107 at 116—117. This was a case under, s. 55(1)'s predecessor provision, s. 29 of Patents Act 1907, and actually dealt with the issue of sub-contractors rather than with implied authority as such. The dispute before me was instead about the extent to which express authorisation to do a specific act thereby implied an authorisation to infringe a specific patent. There was also a lesser dispute about whether express authorisation to do a specific act thereby implied an authorisation to carry out ancillary acts, such as testing. The parties treated the latter as being more of a dispute of fact rather than one of law and I shall do likewise.
Does express authorisation to do a specific act (or to perform a specific process) thereby imply an authorisation to infringe a specific patent?
- If I can look forward to the facts for just a moment, the reason why this matters is as follows. There is no dispute that, under the MTPAS scheme, Vodafone were authorised in writing by a government department to provide priority access to their network for emergency responders (i.e. users in classes 12, 13 and 14), but the authorisation in question said nothing about any particular patents.
- As the argument developed it became clear that the issue was whether, in order to establish a defence of Crown use to a claim for infringement of patent X, s 55 requires:
1. An express authorisation to work the specific patent in question (eg "you are hereby authorised to work patent X"); or
2. A written authorisation which does not expressly identify the specific patent in question, but where the circumstances are such that it is not possible for the authorised party to carry out the instruction in any way that would not infringe the patent (eg "you are hereby authorised to operate process Y/make product Z", in circumstances where this necessarily involves infringement of patent X); or
3. A written authorisation similar to that in scenario 2, but where the circumstances are such that it is not shown to be necessary to infringe patent X when carrying out the authorised act; or
4. Something else.
- These refinements are important for a number of reasons. One is that under s 55(7), the relevant government department "shall", subject to the public interest:
(a) notify the proprietor of the relevant patent "as soon as practicable" after either the patent is granted or the use is started (whichever is the later), and
(b) "furnish him with such information as to the extent of the use as he may from time to time require".
- As Vodafone pointed out, any requirement that the relevant patent should be expressly identified might place a heavy burden on the Crown in a field, such as mobile phones, where a large number of patents might potentially be infringed by any given product or process. For instance the relevant government department might have to identify all the acts that the government department and/or its agents may wish to carry out; identify any patent that might arguably be infringed by any one or more of those acts; analyse (and, more realistically, engage advice to help with) the risk of infringement of each such patent by each such act; identify and engage with each relevant rightsholder; and give notice of each of the relevant proposed acts to the respective rightsholders "as soon as practicable" after the relevant triggering event. Even if this sufficed for purposes of s 55(7), there would still be the matter of actually reaching agreement with each such rightsholder as to the infringement position. Vodafone submitted that it would be difficult enough to complete the relevant tasks even when given plenty of time, but if they had to be completed before the infringing act was done at all then this might be impossible (a fortiori in the event of an act which had to be done in an emergency or other urgent situation). Hence, said Vodafone, if s 55 were restricted to the first scenario then it would be unworkable in many cases.
- The Comptroller acknowledged the force of this argument but resisted the idea that every time the government issued a functional specification or contract, it could be held to have issued a Crown authorisation. The Comptroller also drew attention to Article 31 of TRIPS, which essentially deals with compulsory licensing and government use of patents. It says this, my emphasis:
"Other Use Without Authorization of the Right Holder
Where the law of a Member allows for other use of the subject matter of a patent without the authorization of the right holder, including use by the government or third parties authorized by the government, the following provisions shall be respected:
(a) authorization of such use shall be considered on its individual merits;
(b) such use may only be permitted if, prior to such use, the proposed user has made efforts to obtain authorization from the right holder on reasonable commercial terms and conditions and that such efforts have not been successful within a reasonable period of time. This requirement may be waived by a Member in the case of a national emergency or other circumstances of extreme urgency or in cases of public non-commercial use. In situations of national emergency or other circumstances of extreme urgency, the right holder shall, nevertheless, be notified as soon as reasonably practicable. In the case of public non-commercial use, where the government or contractor, without making a patent search, knows or has demonstrable grounds to know that a valid patent is or will be used by or for the government, the right holder shall be informed promptly;…"
- The Comptroller submitted that any Crown use therefore had to be considered on an individual merit (ie case by case) basis and that ordinarily some form of negotiation (meaning negotiation with the relevant patentee) should have occurred before Crown use was invoked. He resisted the idea that Crown use could be implied where the government had not knowingly authorised the use of a patented invention.
- For these reasons the Comptroller submitted, as did IPCom, that if there were no express reference to a patent in the written authorisation to perform the relevant act, then scenario 2 was the minimum which had to be satisfied in order to establish Crown use in relation to that act. The Comptroller also submitted that scenario 2 considerably reduced the burden on the Crown which Vodafone had identified, and it could be reduced still further by shifting the burden of identifying any relevant intellectual property on to the contractor.
- I do not find this latter point a convincing justification for scenario 2 since it does not seem to reduce the burden at all, which might therefore remain unmanageable in many cases. At most it simply shifts the burden from one person to another.
- I was only referred to two previous cases which shed any light on this issue and this point was not central to either of them. The first in time is Dixon v The London Small Arms Company Ltd (1876) 1 App. Cas 632, HL. This was heard prior to the Patents, Designs, and Trade Marks Act 1883, at a time when a patent had no effect against the Crown. The Secretary of War issued a tender for the supply of 13 875 Martini-Henry rifles, and the defendant employed a patented process in the manufacture thereof. The House of Lords held that the defendant was not an officer, servant or agent of the Crown (in which case he would have had a defence) but merely a "tradesman" or contractor. That was enough to decide the case for the claimant.
- The defendant also ran an additional argument that the Crown had not authorized the use of the patented process. As to this, Lord O'Hagan held as follows, my emphasis:
"The order 'to provide and deliver' involved neither requirement nor approval of illegality, and cannot be assumed to have been issued with the desire that the contractor should act without the permission of the patentee, and therefore, so far as he was concerned, in fraud of individual right and in contravention of the law. Surely, the contrary assumption, if any, should be made. If the work could be done in one of two ways—legally or otherwise—ought we to suppose that the legal mode was not contemplated, in the absence of clear words forbidding it?"
- The only other Lord to consider this argument was Lord Penzance. He agreed with Lord O'Hagan but with some diffidence. See below, my emphasis:
"But I cannot help thinking that … any bare contract … with an agent to do the work, if the Crown says nothing to the effect that he is to do it without reference to a patentee's rights, will not be sufficient to shew that the Crown was exercising such an election, and consequently the agent, without such express authority, would have no right to infringe the patent. My Lords, I say that with some hesitation, because my noble and learned friend on the woolsack appeared to think otherwise. It is not perhaps material in this case …."
The upshot is that Dixon is not conclusive on the point.
- What happened next is that Parliament introduced an express Crown use provision (including provision for compensation) into s 27 of the 1883 Act, which then became s 29 of the Patents and Designs Act 1907. This, along with Dixon, was considered by PO Lawrence J in Pyrene Co Ltd v Webb Lamp Co Ltd (1920) 37 RPC 57, the second case to which I was referred. Pyrene involved the supply of fire extinguishers to the Ministry of Munitions during the First World War. In particular, the Minister contracted with the defendant for a particular type of fire extinguisher and the only defence to infringement was Crown use under s 29. The claimant argued that unless the contract "expressly or by necessary implication provides that" the defendant had to use the patented invention, that defence failed. PO Lawrence J held that "In my view, this contention is too wide" but he did not need to express a concluded opinion since he found that the infringement was necessary anyway (see pages 65 lines 19-28). Hence Pyrene is inconclusive as well.
- In my view the correct answer to the question is scenario 3, ie that provided that the written authorisation identifies the relevant act then Crown use is established. In particular it need not be shown that it is necessary to infringe patent X when carrying out that authorised act in order for there to be a defence of Crown use to a claim of infringement of patent X. I reach this conclusion for the following reasons:
1) First, it seems to me that this is the most natural reading of s 55 in the first place. The authorisation is to do the relevant acts, and if these acts happen to infringe then there is a defence. Nothing in s 55 says that the authorisation has to expressly refer to the patent or that infringement must be essential.
2) Secondly nobody is seriously arguing for scenario 1 (or 4) and the case law shows a divergence of non-binding judicial opinion between scenarios 2 and 3. Hence both are open to me.
3) Thirdly scenario 3 seems much easier to operate in practice than scenario 2. In scenario 3, the only real issue in relation to whether Crown use is established is whether the act done was duly authorised. In scenario 2, there is a raft of secondary questions as to whether it was also "necessary" to infringe patent X.
4) Fourthly, as Vodafone pointed out, scenario 2 is difficult to operate when there is a choice of only 2 routes, each of which infringes a different patent. Eg if the defendant were sued in 2 different actions for infringement of patents A and B by reason of the same act, then presumably any Crown use defence would fail in both actions because in action A it was possible to do the act without infringing patent A, and in action B it was possible to do the act without infringing patent B.
5) Fifthly, choosing between scenarios 2 and 3 is really a question of policy. Who bears more responsibility for infringement, the person authorising the acts or the person doing them? The relevant burden has to be imposed on someone and it seems to me that it more fairly rests with the person authorising the acts in the first place. That said, I can see no obvious reason why such a person could not protect his or her financial position by way of contractual indemnities.
- Does Article 31 of TRIPS make a difference to this question? In my view it does not lean more in favour of scenario 2 then scenario 3, and it is therefore neutral as between them. It also seems to me that Art 31(b) does not specify what sort of "efforts to obtain authorization from the right holder on reasonable commercial terms and conditions" are necessary prior to such use, but it seems unlikely that it would require disproportionate effort.
- Vodafone also drew attention to the exceptions in Article 31 for "other circumstances of extreme urgency or in cases of public non-commercial use". I do not think anything turns on these exceptions. They might be relevant when considering Vodafone's specific acts in this case, but that would not provide an answer to the question as to which of the potential scenarios is consistent with Article 31 generally.
- The key questions, therefore, are whether Vodafone's use is of such a nature that it falls within the non-exhaustive scope of s 56(2) and whether it otherwise satisfies the requirements of the defence. Accordingly I turn to the facts.
Analysis
- The Mobile Telecommunications Privileged Access Scheme ("MTPAS") is the successor to something called the Access Overload Control Scheme. The MTPAS rules are set out in a document produced by the Cabinet Office Civil Contingencies Secretariat, of which the current version (v4.01) is dated March 2019. This document describes the Cabinet Office as the "owner of MTPAS" and sets out how the scheme works. In short MTPAS provides privileged access to mobile phone networks to organisations involved in responding to an "Emergency" as defined in the Civil Contingencies Act 1994. It is activated by way of a request sent to mobile phone networks by or on behalf of the senior police offer in charge of the emergency response (known as the Police Gold Commander). The format of this request is set out in a memo which was sent by the Cabinet Office to Chief Constables in March 2008: see Annex A thereof. More specifically, the MTPAS protocol is activated by an initial telephone call, which is then followed up with "a completed form sent by either email or facsimile … as the official notification and written audit trail": see s 6 of the MTPAS rules document, at [80]. When Vodafone receives such a request, but not before, it activates access control in line with the request it has received. Vodafone does not charge for this service.
- Vodafone submits that on these facts the Crown use defence is made out in relation to all acts done in relation to MTPAS. IPCom disagrees for the following reasons.
a) First, it submits that use pursuant to the MTPAS scheme falls outside the scope of s 56(2) in any event.
b) Secondly that any express permission by the Crown did not include implicit permission to infringe the Patent. This, says IPCom, means that the defence does not run at all. Furthermore Vodafone's own case is that it is possible to comply with MTPAS requests without infringing the Patent (eg using the fundamental redesign).
c) Thirdly, and more specifically, use of the method for purpose of testing is not included; nor is keeping equipment so as to respond to an MTPAS request.
- I begin with the first point. When Vodafone activates the MTPAS scheme, it does so at the request of a Police Gold Commander who is acting pursuant to Cabinet Office authority. The whole purpose of the exercise is to provide the emergency services with priority access to the mobile phone network in an emergency situation. This is done so that the emergency services can best help the public, as well as helping and protecting the emergency responders themselves. Whatever the precise limits of s 56(2), I am satisfied that this constitutes use "for the services of the Crown". I also agree with Vodafone that this conclusion follows on both the majority and minority reasoning in Pfizer, since the use does benefit the Crown directly as well as constituting use by members of Crown services in the course of their duties.
- The second point depends on my conclusion on the relevant law, above. It is true that the MTPAS scheme does not grant express permission to infringe this patent or indeed any patent. Indeed the MTPAS scheme does not even require that LTE be used, merely that the relevant emergency services are given privileged access to the relevant mobile phone networks. However in my judgment this is no bar in law to the Crown use defence succeeding. What matters is the written authorisation to do the relevant act, and it was not disputed (subject to the point about testing) that Vodafone was given such authorisation. It is not necessary for Vodafone also to show that it was necessary for them to infringe the patent. I therefore reject this part of IPCom's argument.
- In case it matters, I do not agree with Vodafone that its participation in the scheme amounts to a "public non-commercial use". Instead I agree with IPCom that this forms part of commercially operating a multi-billion-pound telecommunications network business under the licence of the UK government. However I do accept that individual requests to Vodafone from the Police Gold Commander are likely to qualify as being "other circumstances of extreme urgency". I also accept that if s 55 required the steps identified in paragraph [194] above to be completed in relation to the then-current state of the patent register before the Police Gold Commander could lawfully send such a request, then third party patent rights would thereby stand in the way of the government protecting its own citizens in an emergency. That seems unlikely.
- The third point raises the question of the scope of the permission to be implied in the circumstances described. I agree with Vodafone that if it is to be able to respond to a genuine request when received, it must be able to test its own ability to do so. This includes Vodafone's use of special access classes 11 and 15, even though these particular classes are for their own use not for that of the emergency services. I am confident that both the Cabinet Office and Chief Constables would expect as much, as would the public generally. IPCom did not suggest (eg) that Vodafone was doing too much MTPAS testing, or that Vodafone was doing it in bad faith, or that Vodafone was using its MTPAS testing as a cover for other activities. Nor did IPCom attempt to justify the logic of a position whereby Vodafone was not allowed to test whether the emergency system which it was required to provide would actually work in an emergency. In these circumstances I find that the defence extends to MTPAS testing. In addition I agree that the defence would also apply to the keeping of equipment which infringes claim 13, for so long as the MTPAS request is in operation.
- In conclusion I agree with Vodafone. The Crown use defence is made out to the extent indicated above.
De minimis
Legal context
- As Lord Phillips of Worth Matravers stated in Sienkiewicz v Greif (UK) Ltd [2011] UKSC 10, [2011] 2 AC 229 at [108]:
"I doubt whether it is ever possible to define, in quantitative terms, what for the purposes of the application of any principle of law is de minimis. This must be a question for the judge on the facts of the particular case."
- That said, there is now a body of law considering the de minimis principle in relation to patent infringement. This was reviewed by Arnold J in Napp v Dr Reddy's Laboratories [2016] EWHC 1517 (Pat) at [136]-[139]. As Arnold J explained, it is important to consider both the scale and the nature of the act (or acts) said to be de minimis in the context of the relevant infringement. For instance:
a) In Hoechst v BP [1998] FSR 586 the issue was whether a day's production infringed, but a day's production was still 800 tonnes of material which was a substantial quantity on any view: see [140].
b) In Monsanto v Cargill [2007] EWHC 2257 (Pat) there was a suggestion that 5% of the original, infringing, DNA was present in the commercial product: see [142].
c) In Napp v Ratiopharm [2009] EWCA Civ 252, 7% of the Defendants' tablets had dissolution rates within the claim: a modest, but nevertheless significant proportion: see [143]-[144].
d) Conversely in Napp v Dr Reddy's itself, the proposed scenario (it being a quia timet action) was 200 infringing patches out of 2 million patches sold: see [147].
- The present context is different. It does not involve the production of a small amount of infringing by-product during a process which, as a whole, does not infringe. On the contrary it involves a process which is only performed in rare situations in the first place. IPCom drew a useful analogy with a patent for emergency equipment such as life jackets. One would hope that the life jackets are hardly ever used, if at all, but the point of keeping such equipment is that it is available if and when required. Similarly IPCom submitted that Vodafone has to be ready to implement access control on its network in any part of the country as soon as it is necessary to do so, even if in practice this is not very often. I accept this too, although less turns on it.
- Vodafone made 2 additional submissions, as follows:
a) Vodafone submitted that it was relevant to consider whether the alleged infringer knew that the accused acts would infringe – not because there was a mens rea, but because evidence of such knowledge might negative a case that the rare events of infringement are transient, uncontrolled spikes.
I agree with this up to a point but would express it differently. First, the infringer's intention cannot be directly relevant (see Hoechst v BP at [28]) but it may negative any suggestion that rare events of infringement are accidental. Secondly I do not see why the infringer's knowledge that what he or she is doing actually amounts to an infringement is relevant. For instance if the infringer produces 800 tons of infringing product I cannot see why it should become de minimis if the infringer did not know it infringed.
b) Secondly, Vodafone submitted that the use had to be of commercial significance including whether the infringed in fact made any profit.
I agree that whether the use is commercially significant is a relevant factor (see again Hoechst v BP at [28]), but I cannot see why the infringer's profit is relevant. As IPCom submitted, if the patent is for life jackets then it would not be a defence for the infringer to say that the life jackets were expensive and it lost money on them.
Analysis
- I have set out the detail of all Vodafone's acts alleged to infringe in the Confidential Annex. This refers to acts in Vodafone's confidential PPD at Annexes C, E, and F (which IPCom grouped together as "Group 1") and Annex B ("Group 2"), as well as the factual extent of its participation in MTPAS. In fact it turns out that Annex C forms part of Vodafone's MTPAS response.
- In closing Vodafone relied upon the de minimis defence in relation to each of a) testing pursuant to Vodafone's participation in MTPAS; b) Annex E c) Annex F (see Vodafone's closing at [325]. I have already concluded that the Crown use defence succeeds in relation to MTPAS/Annex C but I will consider that part of the de minimis argument in any event.
- I will here summarise the extent of the acts said to be de minimis as follows.
a) MTPAS testing takes place (1) every few weeks, for a few minutes, on a few base stations; and (2) on a larger scale up to 3 times a year, for up to a few hours, on tens of base stations.
b) Annex E acts took place on less than 10 base stations.
c) Annex F acts took place over a 5 month period on 10 base stations.
- There is no doubt that in each case the actual volume of the acts concerned was very small. However given that access control is not performed in normal operation, but (in general) only in extreme circumstances, the fact that the actual volume of the acts is very small is not surprising. On the contrary it is what one would expect. Moreover Vodafone's intention is not directly relevant, so to characterise them as "inadvertent" is not an answer either.
- Finally I do not accept that just because the acts were performed on a small scale they are commercially insignificant, given the context. For instance Vodafone does not charge the Crown for providing its response under MTPAS, nor for its MTPAS testing. However I consider that its participation in MTPAS, taken as a whole, is a small but significant part of Vodafone's commercial operations as a network provider. The same is less true of the other acts said to be de minimis, but I do not accept that they are such that Vodafone must be allowed to use somebody else's invention with impunity (which is the end point of its argument, stripped of the Latin tag). The extent of relief to be granted may be another matter.
- For all these reasons I reject the defence of de minimis use. It follows that all acts done in relation to Annexes E and F base stations in IPCom's Group 1 infringe the method claims. So too would have acts done in relation to Annex C, had it not been for the Crown use defence in relation to Vodafone's MTPAS testing.
"set up to send"
- Again I have set out the relevant detail in the Confidential Annex. The first point is that whilst Vodafone is actually operating an infringing method, then it was not disputed that the keeping, use, etc of Annex B base stations when modified so that they did perform such method also infringed the product claims. However nothing much appears to turn on this, eg as regards damages.
- The second point is that changing a base station from one which does not operate an infringing method (ie Annex B in normal use) into one which does, is not as simple as choosing whether or not to supply power to it. Assume for the moment that the base station is not transmitting any barring parameters. Now assume that the operator wants to transmit the barring parameters for purposes of access control. The fact evidence established that making the change was not a simple matter of supplying power. On the contrary Vodafone's evidence shows that the change requires reprogramming the base station software.
- IPCom submitted that the reprogramming was akin to flicking a switch. I disagree. I agree with IPCom that the extent of the reprogramming might vary between what Mr Bishop accepted was quite a trivial change (eg a change to the base station software which reads the configuration file, if one has the base station software source code) to a wholesale rewrite of the relevant software, but the fact remains that until the additional programming is done – however extensive or otherwise that additional programming is – the base station does not send the barring parameters. Nor is it adapted or configured to send them. On the contrary, it is adapted and configured not to send the barring parameters.
- From time to time during the trial IPCom advanced a variant of this argument whereby it said that Vodafone's apparatus was at all times "capable of" being used to send the barring parameters, and hence at all times infringed the apparatus claims. I reject this because I have rejected the argument that this is how unconditional claim 13 should be interpreted. In any event this argument ignores the facts as to what actually needs to be done in order to change a base station which does not send the barring parameters into one which does.
- It follows that in normal use (ie when the base stations are not sending the barring parameters) then the keeping, etc of Annex B base stations does not infringe unconditional claim 13 of the Patent or claims dependent thereon.
S 60(2) infringement in relation to SIM cards
- It was not initially clear to me what this argument added. During the course of argument it emerged that it went to damages. Specifically IPCom's case is that each and every time Vodafone supplied a SIM card, they were thereby supplying means relating to an essential element of the invention claimed in unconditional claims 1, 3a, 13, 13a and conditional claims 1 and 7. Importantly, IPCom's case about the supply of SIM cards was not tied to any specific instances of Vodafone operating the infringing method. IPCom's case was that if millions of SIM cards were supplied over a 20 year period, then even if no barring parameters were ever transmitted over that period, every single act of SIM card supply still infringed.
Legal context
- S 60(2) provides as follows:
"(2) Subject to the following provisions of this section, a person (other than the proprietor of the patent) also infringes a patent for an invention if, while the patent is in force and without the consent of the proprietor, he supplies or offers to supply in the United Kingdom a person other than a licensee or other person entitled to work the invention with any of the means, relating to an essential element of the invention, for putting the invention into effect when he knows, or it is obvious to a reasonable person in the circumstances, that those means are suitable for putting, and are intended to put, the invention into effect in the United Kingdom.
(3) Subsection (2) above shall not apply to the supply or offer of a staple commercial product unless the supply or the offer is made for the purpose of inducing the person supplied or, as the case may be, the person to whom the offer is made to do an act which constitutes an infringement of the patent by virtue of subsection (1) above.
- The leading Court of Appeal case is Grimme Landmaschinenfabrik v Scott [2010] EWCA Civ 1110, subsequently considered by Arnold J in Nestec v Dualit [2013] EWHC 923 (Pat), I shall summarise the propositions established by these cases as follows:
1) There can be infringement under s 60(2) even if there is no actual direct infringement: see Grimme at [88]-[90].
2) In order to be "means, relating to an essential element of the invention", the means must contribute to the implementation of the technical teaching of the invention, and not be of completely subordinate importance: Nestec at [176].
3) In order to qualify as a staple commercial product, a product must ordinarily be one which is suppled commercially for a variety of uses: Nestec at [182].
4) In some cases, at least, whether means are suitable for putting the invention into effect depends on whether a person who purchases the product for use in a particular system thereby "makes" that system: see Nestec at [183].
5) The relevant intention is that of the person supplied, or the end user if different: see Grimme at [108]-[109].
6) It is enough if the supplier knows, or it is obvious in the circumstances, that some ultimate users (not freaks) would intend to use, adapt, or alter the "means essential" so as to infringe, or put another way that this is "inherently probable": see Grimme at [112]-[131]. This is to be proved on the balance of probabilities, and it is likely to be the case when the supplier proposes or recommends or even indicates the possibility of such use in his promotional material: ibid [131].
Analysis
- First, I note that IPCom's argument cannot simply be dismissed on the grounds that there is, or may be, no actual direct infringement.
- I also agree with IPCom that the SIM card contributes to the implementation of the technical teaching of the invention, and is not of completely subordinate importance. As IPCom says, the importance of the "subscriber authorisation card" is clear from the description of Figure 4 and the language of the claim. The details of the privileged user classes are derived from the information contained on the SIM card, and this is how the invention distinguishes between "special" users and "normal" users.
- I do not consider that SIM cards are "staple commercial products". It does not seem to me that Vodafone SIM cards are supplied commercially for a variety of uses.
- I do not consider that the question as to whether means are suitable for putting an invention into effect will always turn on whether one is thereby "making" the claimed system, although that was the position in Nestec. Furthermore the discussion in Nestec about "making" is very specific to the patent in that case, which was for a combination of a coffee machine plus capsule. IPCom also reminded me that the reasoning was in fact obiter since the patent was invalid. I will assume for present purposes that SIM cards are suitable for putting the invention of unconditional claims 1 and 13 into effect.
- The issue of intention is a difficult one, since although it is the mobile phone user's intention which is relevant that user is unlikely to have much, if any, idea about access control. The mobile phone user simply wants to use his or her mobile phone. IPCom submitted that this intention was sufficient to establish infringement under s 60(2) (see IPCom's closing at [149]) and I will assume this is correct.
- Where IPCom's argument fails, in my view, is at the last step of the argument – ie that the supplier (Vodafone) knows, or it is obvious to a reasonable person in the circumstances, that the SIM card is suitable for putting, and intended to put, the invention into effect in the United Kingdom. I can see an argument that if Vodafone supplies a SIM card to a user, and Vodafone knows that such user intends to use his or her mobile in an area where Vodafone specifically intends to operate access control on its own network over a particular time period, then Vodafone does have the necessary degree of knowledge. However that was not the basis on which IPCom argued the case.
- IPCom instead argued that the supply of each and every SIM card by Vodafone to its users infringed purely on the grounds that it was possible that Vodafone might some day decide to use the infringing method in relation to that particular SIM card (and modify base stations accordingly). I cannot see how this begins to fix Vodafone with the necessary knowledge for purposes of s 60(2). Whilst I have dismissed Vodafone's defence of de minimis, for any given SIM card and bearing the actual extent of Vodafone's use it remains a remote possibility that such SIM card would ever be used in an infringing method. Nor is there any suggestion that this remote possibility has ever been proposed, recommended, or promoted by Vodafone to its users. This is inherent improbability, not inherent probability.
- Alternatively if one focusses only on the very small number of SIM cards which have in fact been so used, and ignores the difficulty that the act of supply to the user of the SIM card may have been done at one time and the operation of the claimed method by Vodafone may have been done at some other time, I cannot see what the allegation of indirect infringement adds to the allegation of direct infringement. Furthermore Vodafone pointed out some of its LTE services were provided using O2's LTE network, and Vodafone had no knowledge at all as to how O2's network was programmed or operated.
- For all these reasons I reject this part of IPCom's case.
Miscellaneous points
- IPCom ran another case of indirect infringement in relation to its supply of information signals, ie code comprising the barring parameters. This time I do accept IPCom's case on indirect infringement, but only for so long as the information signals are actually being sent. That being so it seems to add nothing to the case of direct infringement of the method claims.
- IPCom made submissions about infringement of the apparatus claims on the grounds that the various parts of the system could be regarded as a kit of parts. I agree with Vodafone that this legal doctrine is currently undeveloped in the UK and that it makes no difference anyway.
Vodafone's applications for declarations of non-infringement
- The importance of Vodafone's applications for DNIs substantially fell away through the trial so I will deal with them briefly.
Legal context
- It was not disputed that any declarations granted by the Court must serve a useful purpose: see eg Carr J in Fujifilm v Abbvie (No. 4) [2017] EWHC 395 (Pat) at [365]-[367]. Moreover they must be clear and not misleading.
Analysis
- The DNIs are sought in respect of the following base stations, each of which is an eNodeB for use in an LTE network in accordance with the LTE standard published by 3GPP. In normal use, none of them transmit any barring parameters (ie ac-BarringConfig). The full details are set out in a PPD devoted to these DNIs and I will merely summarise some features.
a) Alpha. Base station Alpha is not capable of transmitting the parameter ac-BarringConfig and it is not possible to modify it so that it does become so capable. Vodafone accepted that in the real world such a base station would not exist, since in the real world it is always possible to make such a modification.
b) Beta. Base station Beta is not capable of transmitting the parameter ac-BarringConfig because its own software is not so enabled. If a software control management tool instruction to transmit this parameter is sent to the base station, an error message will be generated instead. In order to make Beta capable of transmitting ac-BarringConfig, its own software would have to be changed and installed.
c) Gamma. Base station Gamma is a more extreme version of Beta, in that the software control management tool is not configured in such a way that it could generate an instruction to transmit the parameter ac-BarringConfig in the first place; and nor is the base station's own software configured to send it either. In order to make Gamma capable of transmitting this parameter, both the software control management tool and the base station's own software would have to be changed and installed.
- Both experts agreed that when these 3 stations were operating as described, they did not infringe the method claims, and on the basis of my construction of unconditional claim 13 I find that acts done in relation to them do not infringe any product claims either.
- Even though there is an element of artificiality in relation to Alpha I am satisfied that there is a useful purpose to granting each of the declarations sought and I am prepared to do so. It is true that they do not descend into the detail of a real world system but that is not necessary since each establishes an important point of principle.
- That said, I accept IPCom's submission that since the present case was limited to LTE/4G operation it is important that any declaration granted should be limited accordingly. Vodafone's submission is that because of the way the DNIs are drafted, they are self-limiting to 4G base stations. I will hear counsel as to the precise wording of any declaration which I should grant.
Conclusion
- I will summarise my main conclusions, as follows:
1) The added matter attack against unconditional claim 1 succeeds in part. However the attack on allowability of conditional claim 1 fails.
2) Vodafone's argument of obviousness based on GSM/GPRS and IS-95 fails.
3) If and insofar as the option to perform access control in accordance with 3GPP TS 36.331, version 12 is being exercised, then:
a. unconditional claim 1 would have been essential if it had been valid
b. conditional claim 1 is essential, as is unconditional claim 13; and
c. similar conclusions follow for claims dependent thereon.
4) Vodafone has a good defence of Crown use in relation to acts done in relation to the MTPAS scheme.
5) None of Vodafone's acts of alleged infringement benefits from any de minimis defence.
6) Some of the methods set out in IPCom's Group 1 (namely Annexes E and F to Vodafone's PPD) infringe. The method of Annex C does not infringe, but this is because it benefits from the Crown use defence. Acts done in relation to the apparatus set out in IPCom's Group 2 (ie PPD Annex B) do not infringe.
7) IPCom's allegation of indirect infringement in relation to SIM cards fails.
8) Vodafone's application for DNIs in relation to Alpha, Beta, and Gamma base stations succeeds.
Appendix 1 – conditional claim 1
1. Method for ascertaining an authorization for access to a telecommunication channel (30) of a telecommunication network by a subscriber station (5, 10, 15, 20), wherein information signals sent by a base station (100) with access threshold value and access class information as access authorization data (55) are received by a transmission/reception unit (65) of the subscriber station (5, 10, 15, 20), wherein the access authorization data (55) are transmitted as a bit pattern (55),
wherein the access authorization data comprise access class bits (Z0, Z1, Z2, Z3) as well as access threshold bits (S3, S2, S1, S0), wherein each access class bit represents one user class and wherein each of the user classes is assigned one access class bit,
characterized in that an evaluation unit (60) of the subscriber station (5, 10, 15, 20) has a check (280) performed in it to determine whether an access authorization card (75) of the subscriber station (5, 10, 15, 20) stores an association between the subscriber station (5, 10, 15, 20) and a privileged user class (35, 40) or stores an association of the subscriber station (5, 10, 15, 20) to a normally privileged user class (35, 40), in which it is checked whether an association of the subscriber station (5, 10, 15, 20) to a user class (35, 40) is stored on the access authorization card (75) and whether the user class is a normally privileged user class or a privileged user class,
if an association of the subscriber station (5, 10, 15, 20) to a privileged user class (35, 40) is stored on the access authorization card (75), then the evaluation unit (60) takes the access class bit (Z0, Z1, Z2, Z3) which corresponds to the privileged user class as a basis for checking whether the privileged user class (35, 40) ascertained for the subscriber station (5, 10, 15, 20) is authorized for access to the telecommunication channel (30) irrespective of an access threshold value evaluation,
if this is not the case because an association of the subscriber station (5, 10, 15, 20) with a privileged user class (35, 40) is stored on the access authorization card (75) but the determined privileged user class (35, 40) is not authorized to access the telecommunication channel (30) independent of an access threshold evaluation or if the access authorization card (75) stores no association with a privileged user class (35, 40) because an association of the subscriber station (5, 10, 15, 20) to a normally privileged user class is stored on the access authorization card (75) or no association to a user class (35, 40) is stored on the access authorization card (75), then the evaluation unit (60) performs the access threshold value evaluation with the following steps:
(i) the evaluation unit (60) ascertains an access threshold value (S) from the access threshold bits (S3, S2, S1, S0) of the access authorization data (55),
(ii) draws a random or pseudo-random number (R),
(iii)compares the access threshold value (S) with the random or pseudo-random number (R), and
(iv) allocates an access right for the telecommunication channel (30) to the subscriber station (5, 10, 15, 20) on the basis of the comparison result,
wherein the telecommunication channel is a random access channel.


